
More than 1,000 crushfast institutions currently exposed online are unsafe for abduction of an important security bug attacks, providing administrator access to web interfaces.
Safety vulnerability (Cve-2025-54309) AS2 is incorrect due to verification and affects all crushfast versions below 10.8.5 and 11.3.4_23. The seller actively tagged the defect as an active exploitation in the wild on 19 July, given that the attacks could begin before, although evidence has not yet been found to confirm it.
“0-day exploitation has been seen in the wild in CST at July 18, 9 pm. It is probably going for a long time, but we have seen it then. Hackers clearly reverse our code and found something that we had already decided,” read, ” Crushftp advisor
“They are exploiting it for any person who are not present on new versions. As usual we recommend regularly and frequent patching. Anyone who had kept till date, was spared from this exploitation.”
However, the server added last week that the server that has been updated is not insecure to the attacks, stating that customers who use a dimilitated zone (DMZ) example to separate their main servers are not affected by this vulnerability.
The company also recommends uploading and reviewing download logs for unusual activity, as well as automatic updates and servers enabling the vialisting IP and accessing admins to further reduce exploitation efforts.
As per the scan from the Safety Danger Monitoring Platform Shadowner Stay unplaced against cve-2025-54309 And are unsafe for attacks.
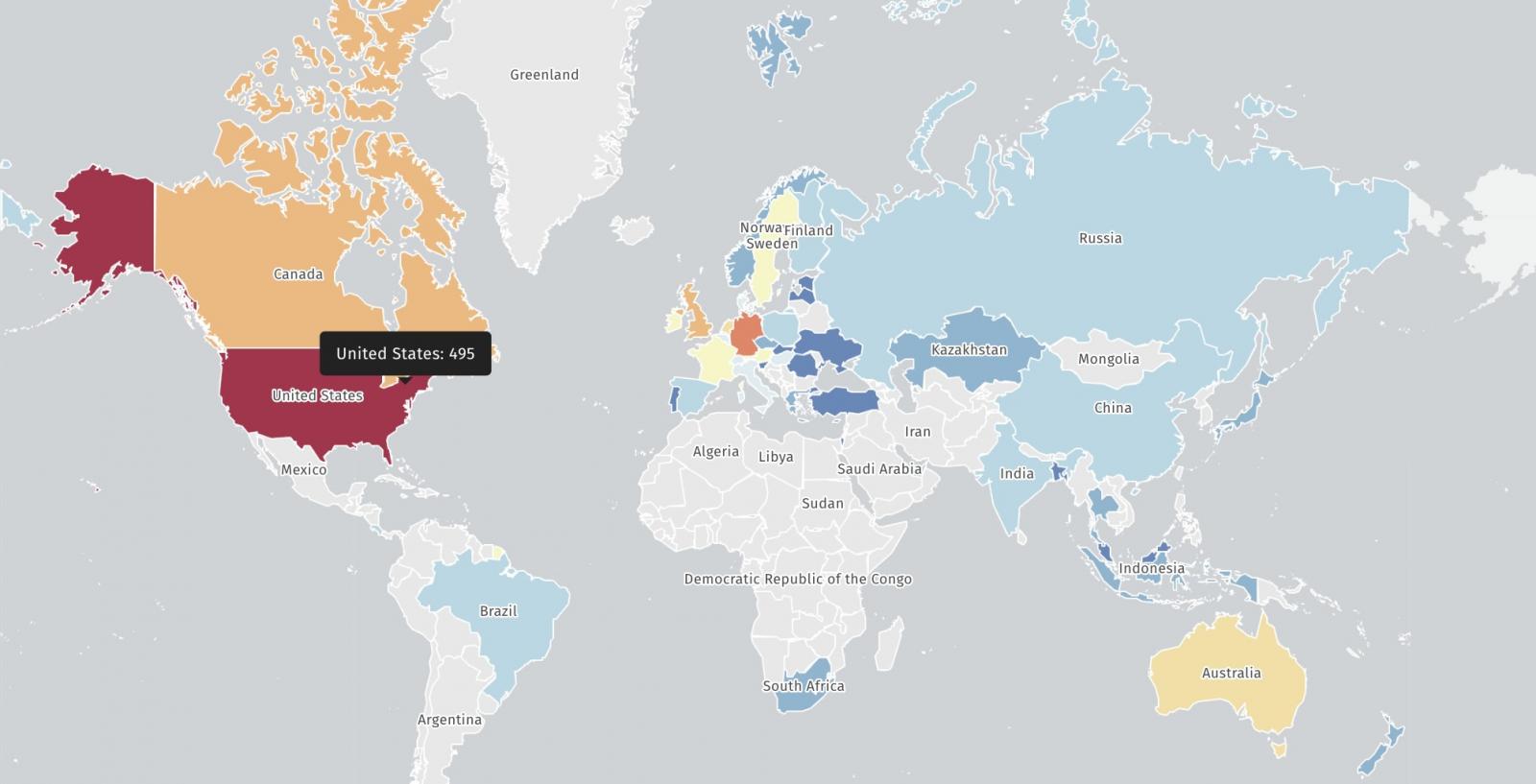
Shadowseerver is Now inform Crushftop customers that their servers are unsafe against exploitation of CVE-2025-54309, which highlight their content for data theft efforts.
Although it is unclear whether these ongoing attacks have deployed malware or used for data theft, in recent years, managed file transfer solutions such as crushfp for ransomware gangs such as crushfp for ransomware gangs are targets of high value.
For example, clop cybercrime gang alone Excelian FTA is associated with many data theft operations targeting zero-day flaws, Goanywhere MFT, Moveit Transfer, and, most recently, Cleo software.
A year ago, in April 2024, Crushafp also tracked an actively exploited zero-day (CVE-2024-4040., This allowed uncontrolled attackers to avoid the user’s virtual file system (VFS) and download system files.
At that time, Cyber Security Company Crowdastric Found proof The attacks, which targeted the crushaft examples in many American organizations and focused on intelligence, were possibly politically motivated.
CISOS knows how to purchase a board begins with a clear, strategic approach how the cloud safety runs the business price.
This helps to introduce the risk, impact and priorities to the free, editable board report deck deck security leaders in clear business terms. Convert security updates into meaningful conversations and take fast decision in boardroom.



