
More than 84,000 roundcube webmail installations are unsafe for CVE-2025-49113, a significant remote code execution (RCE) is a blame with a public exploitation.
The defect, which affects the roundcube versions through 1.6.10 through 1.6.10, was over a decade. Patching on 1 June 2025After the discovery and reporting by safety researcher Kiril Ferresov.
The bug is stems from $ $ _GET (‘_ to’) input, when the session keys compete when the sessions begin with a amazing sign mark, PHP Object Disorganization and Sessions are able to corruption.
Shortly after the patch was released, hackers reverse-engineer to develop a working exploitation, which they sold on underground forums.
Although exploitation Cve-2025-49113 The authentication requires, the attackers claim that legitimate credentials can be obtained through CSRF, log scraping, or cruel-maze.
Firesov shared technical details about the defect On their blog To help protect against active exploitation efforts, which is likely to be too much.
Large -scale risk
Roundcube is widely used in widely shared hosting (Godaddy, hostinger, ovh) and widely used in government, education and technical sectors, with more than 1,200,000 examples online.
Threatening monitoring platform Report of shadowseerver foundation That its internet scans return 84,925 rounds Weak to CVE-2025-49113 by 8 June 2025.
Most of these examples are in the United States (19,500), India (15,500), Germany (13,600), France (3,600), Canada (3,500), and United Kingdom (2,400).
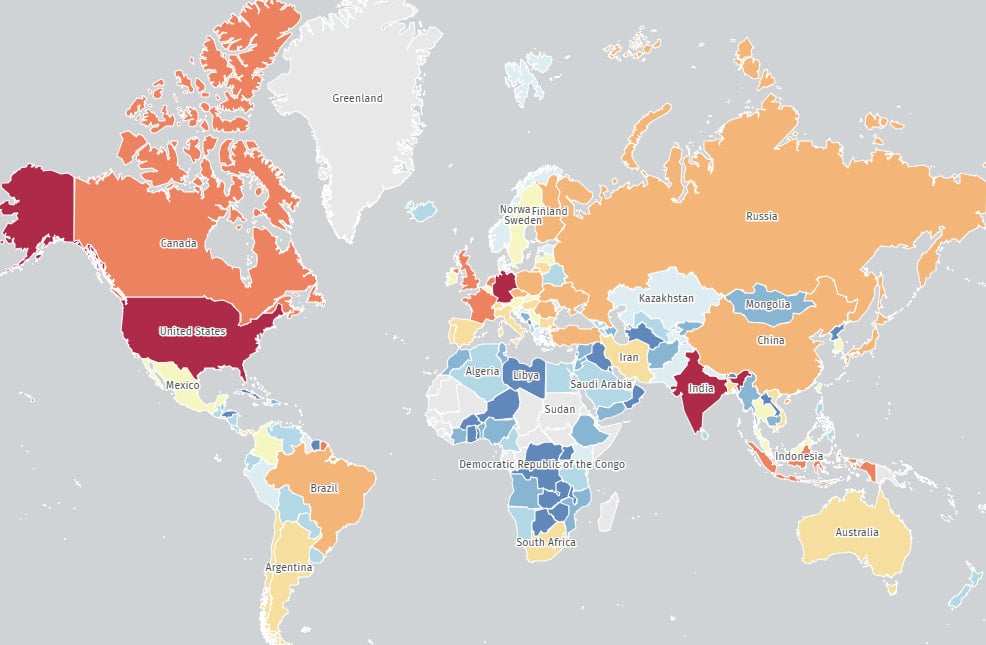
Source: Shadowseerver Foundation
Considering the high risk of exploitation and the ability of data theft, contact of those examples is an important cyber security risk.
System administrators are recommended to update versions 1.6.11 and 1.5.10, which address the CVE-2025–49113 as soon as possible.
It is not clear whether the defect is being done in real attacks and on which scale is being leveraged, but immediate action is recommended.
If it is impossible to upgrade, it is recommended to restrict access to webmels, close the file uploads, add CSRF security, block risky PHP function and monitor for exploitation indicators.



