
Mosila has warned the browser extension developers of an active fishing campaign targeting accounts on its official AMO (addons.mozilla.org) repository.
Mosilla’s add-on platform hosters More than 60,000 browser extensions And More than 500,000 themes Used by millions of users worldwide.
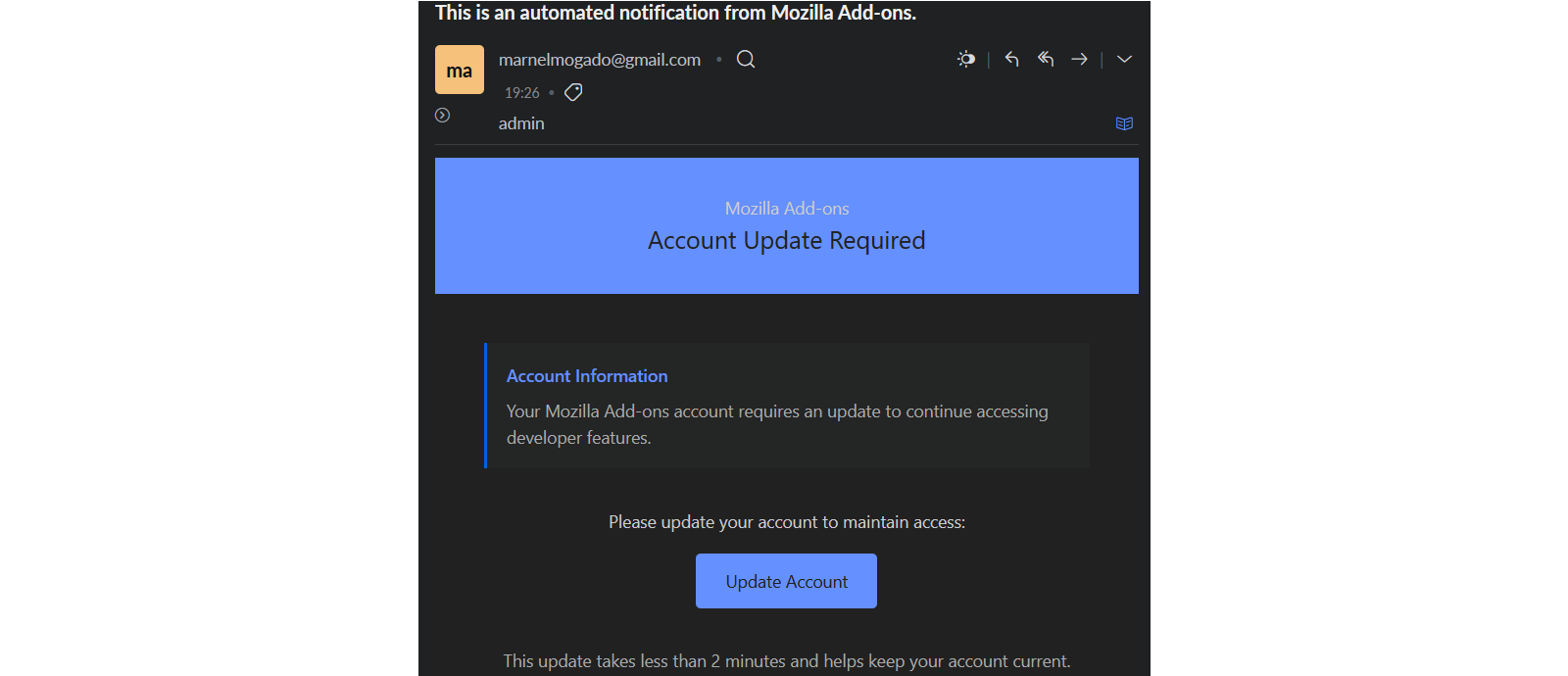
According to Mozilla’s advisor, these fishing emails are implementing the AMO team and claiming that targeted developer accounts require updates to maintain access to development facilities.
“The developer community should know that we have detected a fishing campaign targeting Amo (addons.mozilla.org) accounts. Ad-on developers should take extreme care and check when obtaining emails claiming to be from Mozilla/AMO,” Mozilla warns On Friday.
“Fishing email usually suggests some variation of the message ‘Your Mozilla Ad-on account requires an update to reach the developer facilities.”
To secure their accounts, developers are always advised to verify whether the email they receive are sent from a mozila domain (Firefox.com, Mozilla.org, Mozilla.com, or their sub -domain), that they pass the standard email authentication check (SPF, DKIM, and DMARC) in the email, and doubtful emails. Not to click on the embedded link.
Mosila urged the developers to navigate directly on their websites instead of following the email link, and only enter your login credentials on the official Mozilla or Firefox Domain.
While Mosila has not yet revealed the scale of this fishing campaign, the ultimate goal of the attacks, or whether any developer accounts were already successfully compromised, at least one developer Claim To suffer.
Mosila said that if additional details about this campaign are available, it will provide updates.
The warning came after last month’s announcement that Mozilla’s ad-on operations team has introduced a new security facility to help block the malicious firefox extension designed to drain the cryptocurrency wallet.
Ad-on Operation Manager, Andreas Wagner, who oversees the material safety and reviews the efforts for Addons.Mozilla.org (AMO), said that Mozilla has identified and removed hundreds of extensions including fake cryptocurrency wallets over the years.
While all these extensions were not directly associated with malicious activities, the cyber criminal stole a $ 494 million cryptocurrency last year through a wallet-drying attacks affecting more than 300,000 wallet addresses.



