
A new “Lao Your on Installer” EDR bypass technology is used in attacks to bypass the tampering conservation facility of the watchdog, allowing the danger actors to disable the endpoint detection and response (EDR) agents to establish Babuk Rancemware.
This technique takes advantage of a difference in the agent upgrade process that allows danger actors to run EDR agents, making the equipment unsafe.
The attack discovered this attack during the engagement with a customer by John Isals and AON’s Strose Freedberg event response team, which was facing ransomware attack earlier this year.
Technology does not rely on third-party tools or drivers such as we normally see with the EDR bypass, but rather misuse the Sentinelon installer instead.
Sentinelon recommends customers to enable the “online authority” setting, which is closed by default, to reduce this attack.
“We want to ensure that the term exit to ensure that the customers of Sentinelon have to enable local upgrade safety,” John Alex, AON’s Stroz Freedberg DFIR told BlappingComotar.
“We have examined the atmosphere with Sentinelon as their guidance was sent to customers and has seen customers who still do not enable it. At the end of the day, obtaining words to reduce this bypass is the most important thing.”
Actively exploited in ransomware attacks
Researchers from Stroz Freedberg say that Sentinalon saves its EDR agent with an anti-tamper safety facility, which requires a manual action in the Sentinelon management console or a unique code to remove an agent.
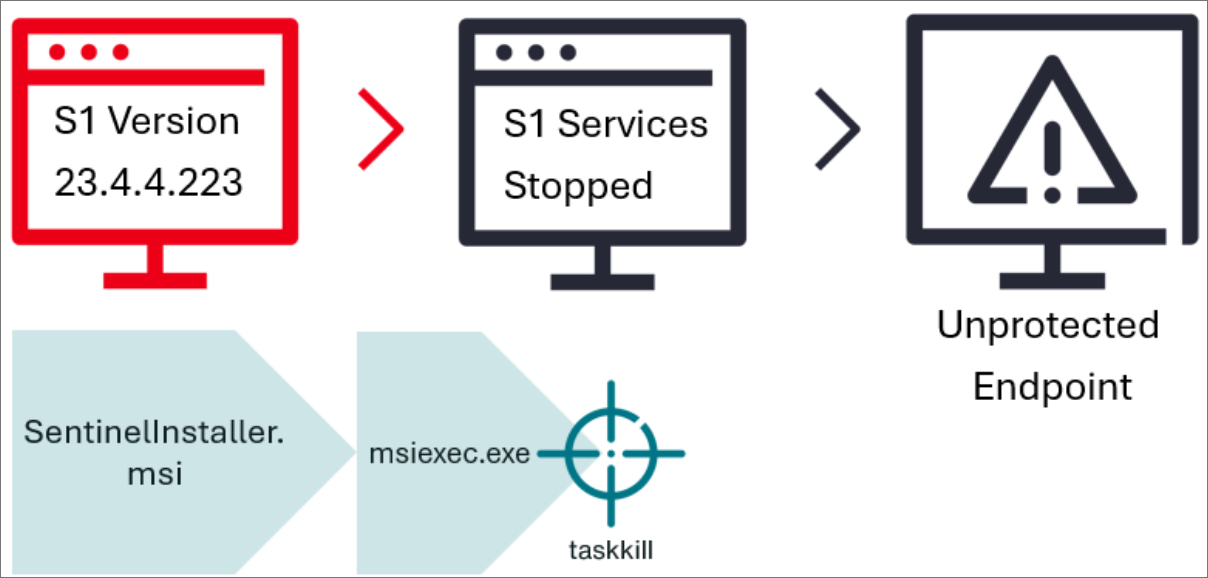
However, like many other software installers, the Sentinelon installer eliminates any affiliated windows processes just before the existing files are adopted with the new version when installing a separate version of the agent.
The danger actors found that they could take advantage of this small window of the opportunity by running a legitimate sentinel installer and then after shutting down the services of the running agent, they could fiercely eliminate the installed process, which makes the equipment unsafe.
Source: Strose Freedberg
Earlier this year, Stroz Freedberg was engaged to check an attack on a customer’s network, showing that the attackers had administrative access to the customer’s network through a vulnerability.
The attackers then used this new bypass by abolishing the Sentinelon Windows Installer (“” “msiexec.exe“) The process before installing and launching the new version of the agent. With disabled security on the device, the danger actors were then able to deploy ransomware.
In a conversation with Bleepingcomputer, AILES stated that the danger actors can use new or old versions of the agent to conduct this attack, so even though the latest versions run on equipment, they are still unsafe.
“Stroz Freedberg also noticed that the Sentinelon management went offline in the Console, shortly after finishing the host installer. Stroz Freedberg’s report,
“Further testing revealed that the attack was successful in several versions of the Sentinelon agent and did not depend on the specific versions seen in the event.”
Strose Freedberg expressed the attack responsibly for Sentinelon, who in January 2025 worked with customers privately.
The mitigation is to enable the “online authority” facility in the Sentry Sentinel Settings, which when enabled, requires the approval from the Sentinelon management console before the local upgrade, downgrade, or uninstall of the agent.
Sentinelon also shared the advice of Stroz Freedberg on this new technique with all other major EDR vendors on this new technology, if they were also affected.
The Palo Alto Network confirmed Strose Freedberg that the attack did not affect its EDR software.



