
A new post-exclusion command-end-control (C2) stolen method called ‘Gost Call’ Abuse Turn Server used by apps used by conferencing apps such as zoom and microsoft teams for tunnel traffic through reliable infrastructure.
Ghost Call uses valid credentials, webrtc and custom tooling to bypass most existing defense and anti-anti-use measures, without relying on an exploitation.
This new strategy was presented praetorianSecurity Researcher Adam Crosser at Black Hat USA, where it was revealed that new technology can be used by red teams when penetrated emulation exercises.
“We take advantage of the web conferencing protocol, which are designed for real-time, low-oppression communication and operated through the globally distributed media server that act as a natural traffic relay,” Presents briefing reads,
“This approach allows operators to blend the interactive C2 sessions in the normal venture traffic patterns, which temporarily appears as nothing more than the online meeting.”
How does ghost call works
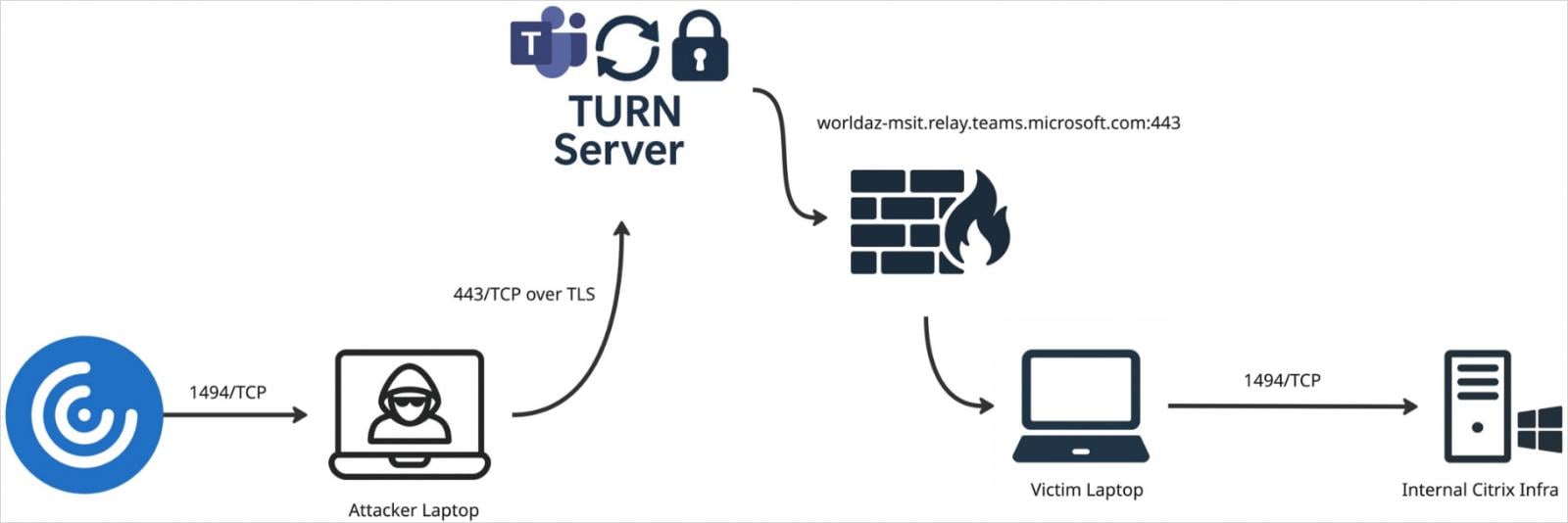
Turn (traverse using relay around NAT) is a networking protocol that is commonly used by video calls, VOIPs, and WebrtC services that help to communicate the devices behind the NAT firewall when a direct connection is not possible when a direct connection is not possible.
When a zoom or team client joins a meeting, he receives temporary turn credentials that ghost calls may kidnap to install a turn-based Webrtc tunnel between the attacker and the victim.
This tunnel can be used to proxy the proxy data or C2 traffic, which is in the form of regular video conferencing traffic through a reliable infrastructure used by zoom or teams.
Since traffic is rooted through valid domains and IPs that are widely used in the enterprise, malicious traffic firewalls, proxies and TLS can bypass inspection. Additionally, Webrtc traffic has been encrypted, so it is well hidden.
By misusing these devices, the attackers also avoid highlighting their own domains and infrastructure by enjoying high performance, reliable connectivity and adaptability to use both UDP and TCP on port 443.
In comparison, traditional C2 mechanisms are slow, specific, and often lack the VNC operations facilitates the real -time exchange capabilities required to facilitate the operation.
Source: Pratorian
Turnat-IT
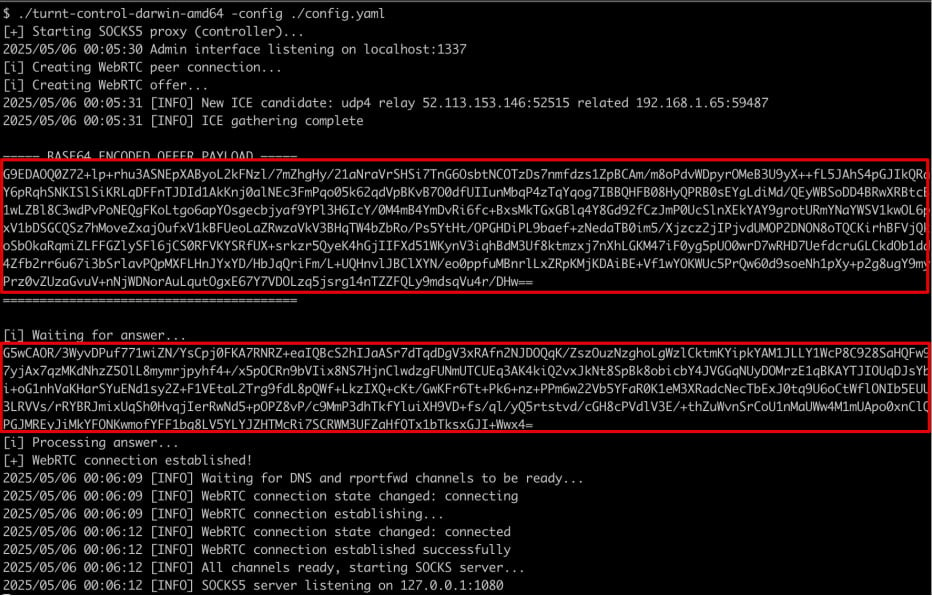
Crosser’s research ended with the development of a custom open-source (Available on github) Utility called ‘Turnat’ can be used for tunling C2 traffic through zoom and Webrtc Turn server provided by teams.
Turnat consists of two components, namely a controller moving towards the attacker, and a relay posted on a compromised host.
The controller runs a sox proxy server to accept the tunled connection through turn. The relay connects back to the controller using the turn credential, and sets a webrtc data channel through the provider’s turn server.
Source: Pratorian
Turnat socks can facilitate proxy, local or remote port forwarding, data exfoliation, and hidden VNC (virtual network computing) traffic tunling.
Although Ghost Call Zoom or Microsoft does not take advantage of any weaknesses in teams, Bleepingcomputer has approached both vendors whether they plan to introduce additional safety measures to reduce their viability. We will update this post once, when we either receive the response.



