
A new Linux Malware called Kosk may have been developed with artificial intelligence and Panda is deploying malware in system memory directly using beer beer of beers.
Researchers at Cyber Security Company analyzed Koskay and described it as a “sophisticated Linux danger”. Depending on the observed adaptive behavior, researchers believe that malware was developed using large language models (LLM) or automation structure.
The purpose of the cosk is to deploy CPU and GPU-un-origned cryptocurrency miners that use computational resources of the hosts for more than 18 different coins.
Aquasec identified the Slovak language in the GITHUB repository that hosted the Serbia-based IP addresses, the Serbian phrases and miners in the scripts used in the attacks, but it could not assure anyone.
Pond attack
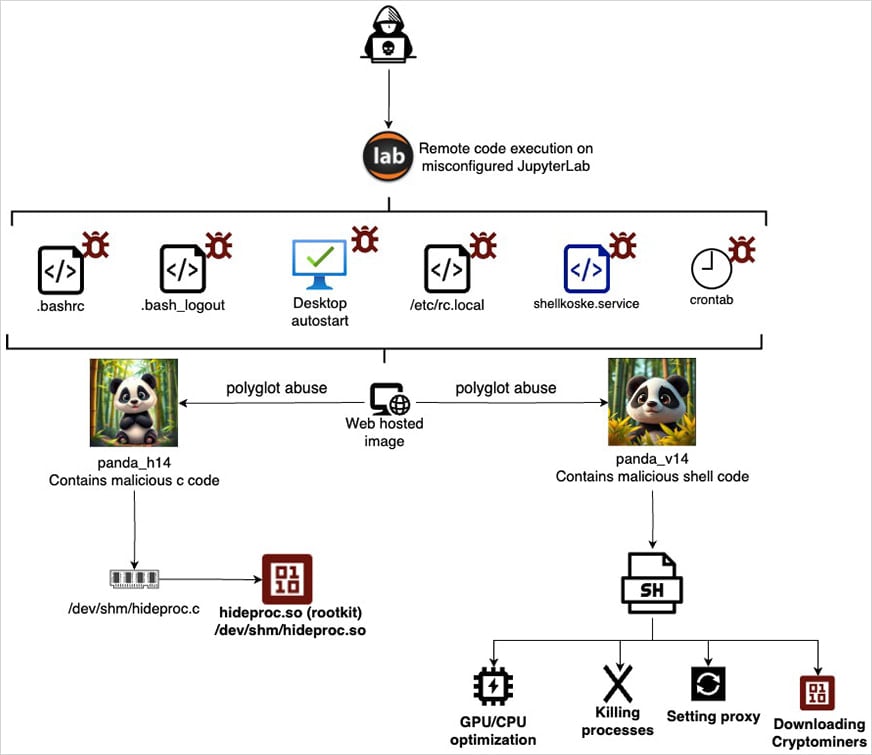
Early access is achieved by taking advantage of the missingfigure of Jupyterlab examples revealed online to achieve command execution.
After one leg, the attacker downloads the images of two .JPEG Panda. However, pictures hide malicious payloads.
The Aquasec underlines that the danger actor did not use stagnography to hide the malware inside the images, but rely on polyglot files, which are valid in many formats.
In cosk attacks, the same file can be interpreted both as an image and script, based on the application that open or process it.
While the panda pics are valid image headers for the JPEG format, they also include malicious shell scripts and C codes at the end, allowing both formats to differentiate differently.
The user opening them will see a cute panda bear, but a script interpreter will execute the enclosed shell code at the end of the interpreter file.
Source: Ekwasak
The attack Ekwasake hid a payload in each image, both were launched in parallel.
“There is a payload C code that is directly written on memory, compiled, and executed as a shared object. Ekwasak explains,
“The second is a shell script, which is also executed by memory, which uses standard systems utilities to run secretly and maintain firmness while leaving some visible scars.”
The shell script is executed by misusing the native Linux utilities directly into the memory, firmness is established through the chrona jobs running every 30 minutes, and the custom systemd Services.
This network also does strict and proxy theft, overwriting /tc/resolv.conf To use Cloudflare and Google DNS, lock it using it Chattr +I Command, flushing iptables, resetting the proxy variables, and using a custom module using a custom module for the proxy working through curls, wet, and raw TCP checks.
This type of adaptability and behavior motivated the untouchable researchers to suspect that the danger actor developed the malware with the help of either LLM or automation platforms.
The C-based rootkit is compiled in memory and uses LD_PRELOAD to override processes, files, and directors from the user-space monitoring tools, hiding the processes, files and directors, readDir () function.
The rootkit coskay, Hidprook, or/DEV/Shm/. Hiddenppid, reads the entries based on string by reading the pids hidden from.
After establishing network access and establishing firmness, the shell script downloads cryptominers from Github.
Source: Ekwasak
Prior to deployment, the host’s CPU and GPU are evaluated to determine which miners will be the most efficient option.
The cosk supports mining for 18 different coins, including hard-to-trace Monero, Revencine, Zano, Nexa and Taur.
If a coin or mining pool becomes unavailable, the malware automatically switchs into backups from its internal list, indicating high levels of automation and adaptability.
Ekwasak has warned that AI-operated malware such as cosk is already concerned, future variants can take advantage of real-time adaptability, developing in more dangerous sections of dangers.



