
Security researchers have revealed a new safe boot bypass tracked as CVE-2025-3052 that can be used to close security on PCs and servers and install bootkit malware.
This defect affects almost every system that rely on Microsoft’s “UEFI CA 2011” certificate, which is a lot of hardware that supports a safe boot.
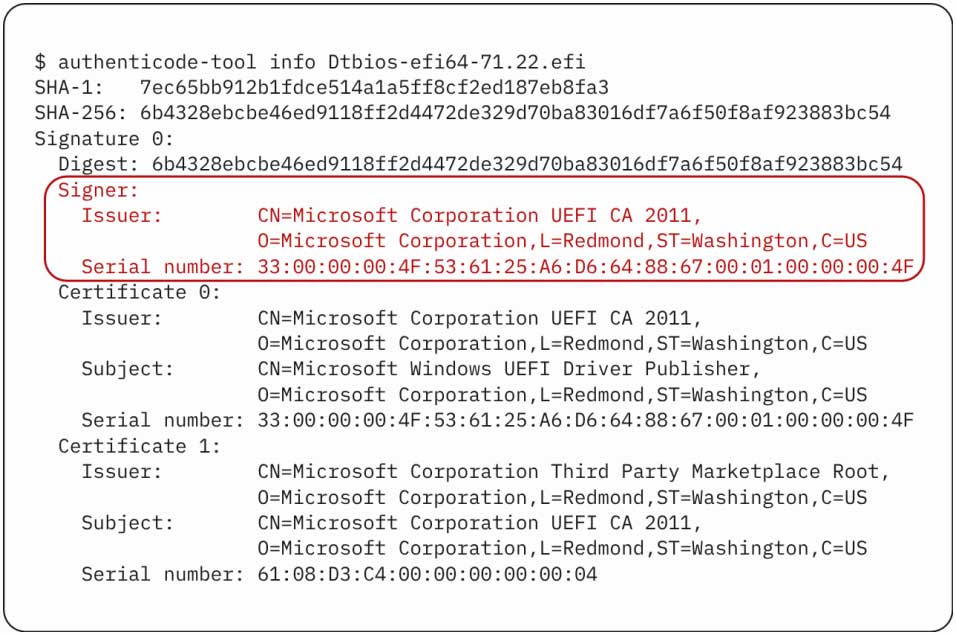
Binarly researcher Alex Matrosov discovered the CVE-2025-3052 defects after discovering Microsoft’s UEFI signing certificate.
The utility was originally designed for rugged pills, but as it was signed with the UEFI certificate of Microsoft, it could run on any safe boot-capable system.
Further investigation revealed that the weak module had been walking in the wild since at least 2022 and was later uploaded to Vishaltal in 2024, where it was seen by Binirli.
Binarly revealed the blame for CERT/CC on 26 February 2025 Cve-2025-3052 Microsoft June 2025 Patch is being reduced today as part of Tuesday.
However, during this process, Microsoft determined that the defect affected 13 other modules, which were added to the cancellation database.
“During the triage process, Microsoft determined that the issue did not start only one module as it was believed to be initially, but really 14 diarrhea modules,” Binrali explains.
“For this reason, the updated DBX released during the patch on Tuesday, June 10, 2025, includes 14 new hash.”
Safe boot bypass
This defect is caused by a valid BIOS update utility signed with Microsoft’s UEFI CA 2011 certificate, which is rely on most modern systems using UEFI firmware.
Source: Binarly
This utility reads a user-writing Nvram without validating the Ihisiparmbuffer. If an attacker has administrator rights for an operating system, they can modify this variable, so arbitrary data is written at memory locations during the UEFI boot process. This is done before the operating system, or even kernels, loaded.
Using this vulnerability, Binarly exploited a proof-off-concept to zero the ‘GSECURITY2’ global variable, which is used to apply a safe boot.
“For our proof of concept (POC), we choose to transmit the global variable GSECURITY2,” tell Binrally report,
“This variable safety keeps an indicator for 2 architectural protocols, which the loadimage function uses to apply a safe boot. By setting it on zero, we disable safe boots safely, allowing any non -composed UEFI module to be executed.”
Once disabled, the attackers can install bootkit malware that can hide from the operating system and close further security features.
To fix the CVE-2025-3052, Microsoft has added the affected module hash to the safe boot DBX cancellation list. Binarly and Microsoft users urge them to immediately install the DBX file updated through today’s safety updates to protect their equipment.
Even today, another safe boot bypass affecting UEFI-Sangat firmware based on Insyde H2O was revealed by Nicolaj Schleze. Shortcoming, Dubbed hydroph 0 bia And the CVE-2025-4275 was tracked, insyde was informed and patched 90 days after the disclosure.
Binarly shared a video that shows how their POC can disable safe boots and cause a message to display before the operating system boots.



