
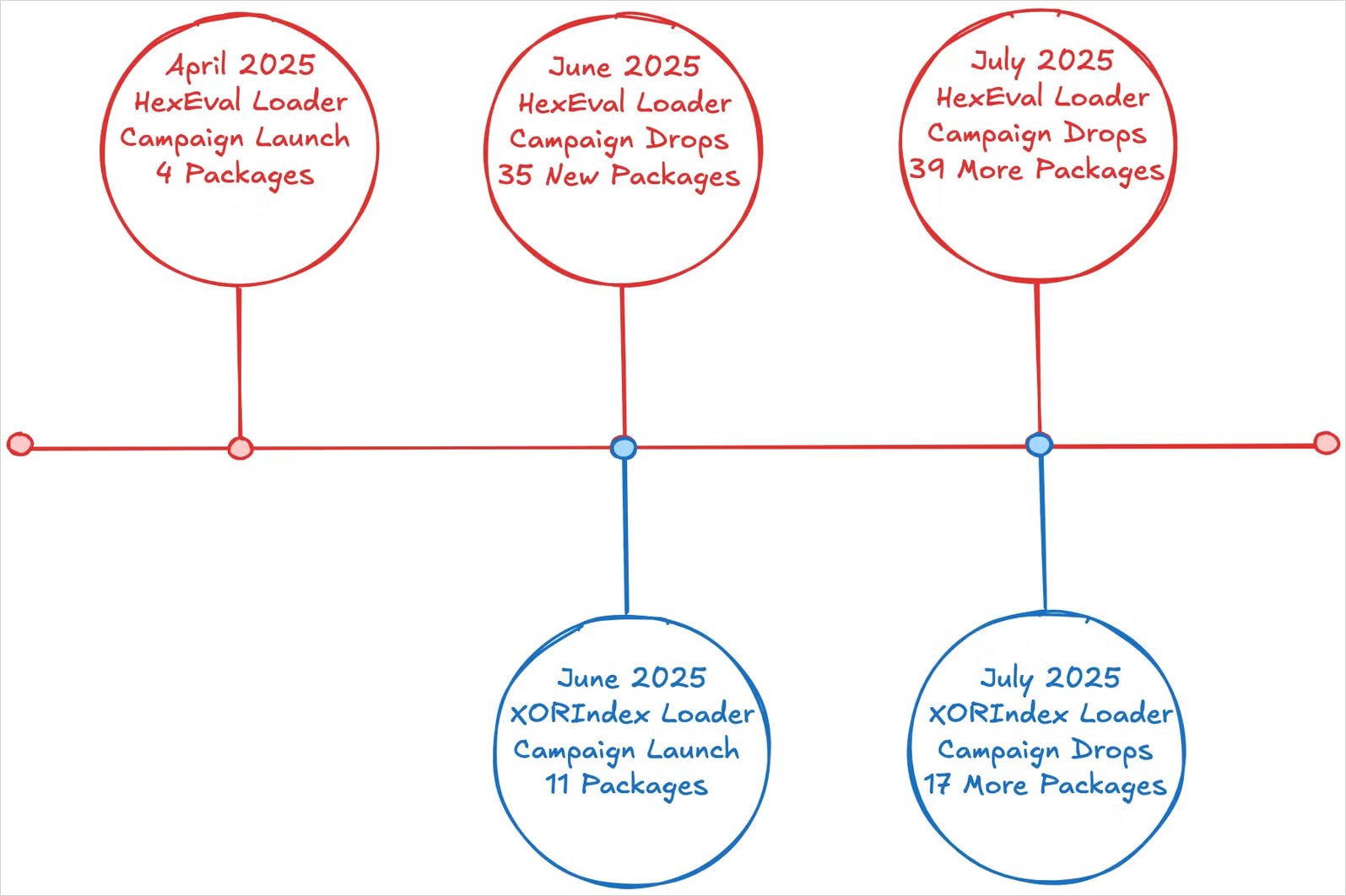
The North Korean threat actors put 67 malicious packages in the Node Package Manager (NPM) online repository, which to give the developer system a new dirtware loader called Xorindex.
The packages collectively count over 17,000 downloads and the package was discovered by researchers in the Security Platform socket, which assess them to be part of constant infectious interview operations.
Researchers at the socket say that the campaign follows the danger activity revealed from April. Last month, the same actor infiltrated the NPM with 35 packages, which demolished information and dropped the backdoor on developers’ equipment.
Source: socket
Overview of attacks
Contegius interview is a North Korean state-supported campaign that targets most developers with fake jobs that trick them to run malicious codes on their systems.
This purpose varies from collecting sensitive information that allows companies to steal cryptocurrency assets.
Node Package Manager (NPM) is a default package manager for Node.JS, a platform where developers publish and install JavaScript library and tools. It is widely used in web development, but is often exploited by danger actors for malware distribution.
Out of 67 packages, this time, many of the danger actors uploaded on NPM are those who mimic or mix the names of legitimate software projects and libraries, such as: such as:
- White-meta-plugin
- vite-postcss-tools
- White-legging
- White-leg
- Beautiful chalk
- North-selection
- JS-Pportyer
- Flow -boundary
- Fig
- MIDD-JS, Middy-JS
When the victims install any of these packages, a ‘poststall’ script is executed to launch Xorindex loader, a novel tool used in parallel with hexwell loaders, a malware dropper seen in previous attacks.
The Xorindex loader collects host data to profile each victim and sends it to a hardcode command and control (C2) address, which is hosted on the infrastructure from Versel Cloud Application Company.
The C2 server reacts with one or more JavaScript payload, which is executed on the victim’s system using eval (). These payloads are usually beepartel and invisible backdoor, both are attributed to North Korean infectious interview operations.
Two pieces of malware provide access to compromised machines, allowing data exfIs, and can download more payloads.
According to the researchers, North Korean hackers combine old and new devices with microscopic modifications, and each time NPM cleans an infection, they return through various NPM accounts and package names.
“An actor of the danger of infectious interview will continue to diversify his malware portfolio, moving through the new NPM vertebrate surnames, loaders such as hexwell loaders and malware families such as beeprtel and invisible, and actively deploy new observation variants including Xorindex loaders, and actively deploy new observation – the sockets – the sockets – the sockets.
Researchers warned, “Guarders should expect continuous recurrence of these loaders in new published packages, often with minor changes to find out,” the researchers warned.
Researchers at the socket say that they reported NPM to all malicious packages from the latest campaign, but some of them may still be available in the repository.
To ensure that they are not typing the decoice, it is important to double-check the sour packages to ensure that only with famous projects and a proven records, and recently for the signals of automation to check the recent repository activity.
When possible, always check the source code for obfusation and execute new libraries in isolated environment to evaluate your safety.



