
O2 In the implementation of the VoLTE and Wifi calling technologies of the UK, a defect can allow anyone to highlight the general place of a person and other identifiers by calling the target.
The problem was discovered by the safety researcher Daniel Williams, who says that the defect was present on the O2 UK network from March 27, 2017, and was resolved yesterday.
The O2 UK is a British telecom service provider owned by Virgin Media O2. By March 2025, the company reported to be around 23 million mobile customers and 5.8 million broadband clients in the UK, putting it as one of the major providers in the country.
In March 2017, the firm launched its IP Multimedia Sub -Service (IMS) service, which is branded as “4G calling” for better audio quality and line reliability during calls.
However, as Williams discovered when analyzing traffic during such calls, the signaling message (SIP header) was exchanged among the transmitted parties, which are very far away and disclosure, including IMSI, IMEI and cell location data.
“The reactions I received from the network were extremely wide and long, and were contrary to anything seen earlier on other networks,” Williams states,
“Messages included information such as the IMS/SIP server is used with version numbers by O2 (Mavenir UAG), processed by C ++ services processed by C ++ services when something went wrong when something went wrong, and other debugging information.”
Source: Mastdatabase.co.uk
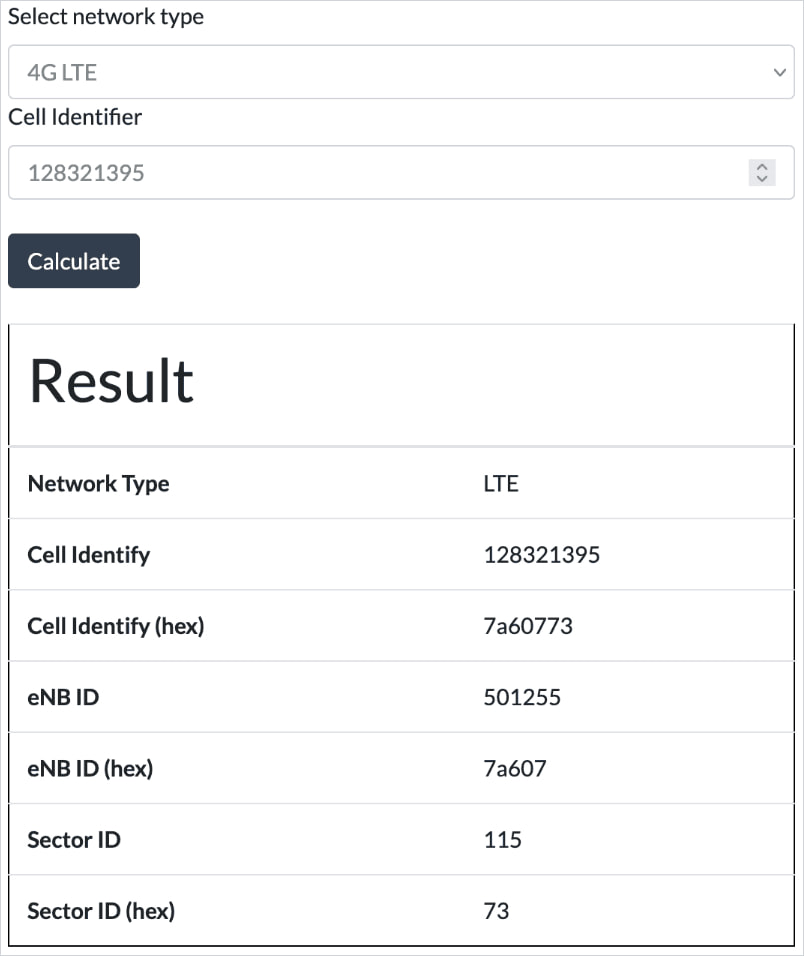
Call to find users by call
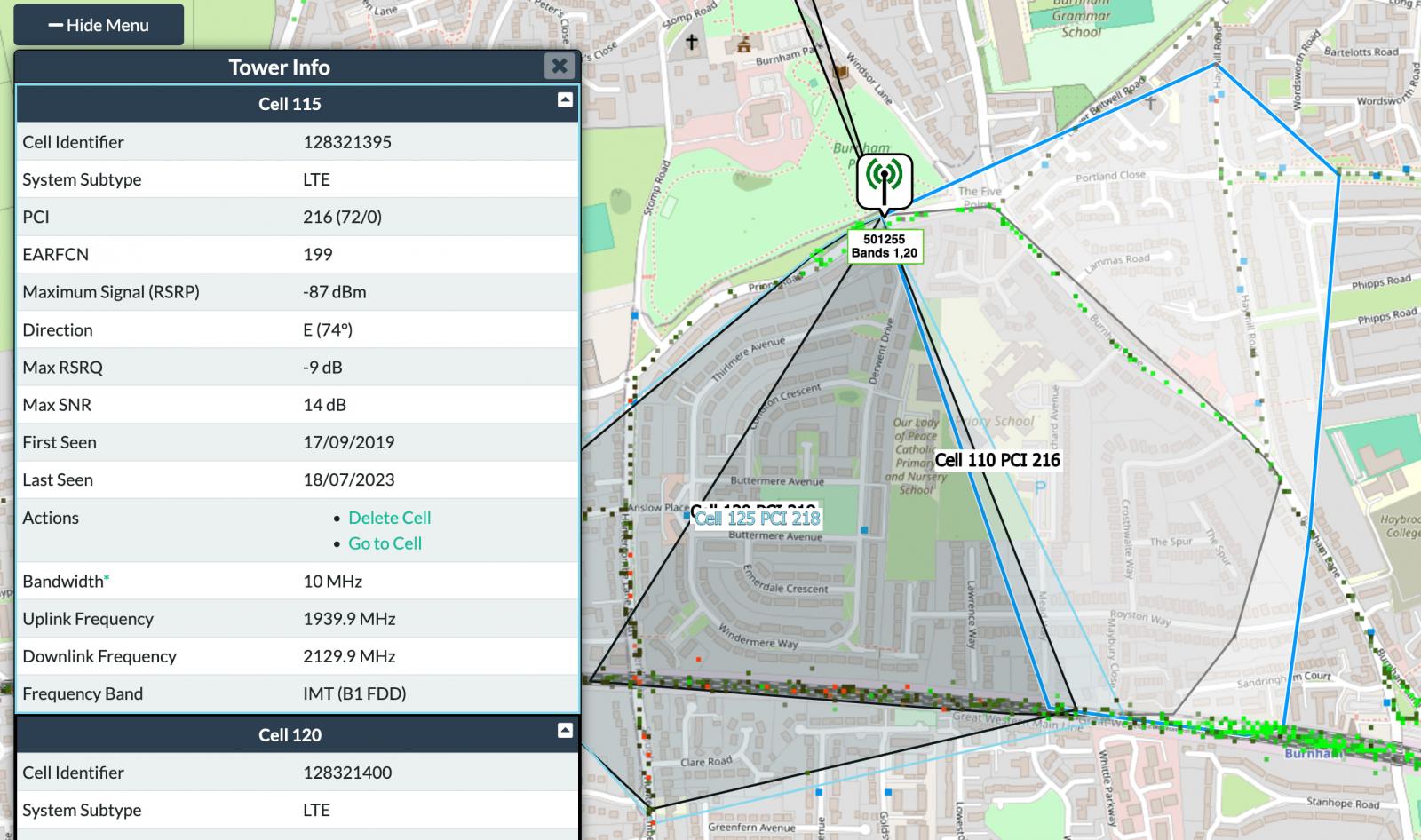
Using the Network Signal Guru (NSG) app on a rooted Google Pixel 8, Williams intercepted the raw IMS signaling messages exchanged during a call and decoded the cell ID so that the final cell tower was connected to the call recipient.
Then, they used public devices that provide cell towers maps to find the geographical coordinates of the tower.
Source: Mastdatabase.co.uk
For urban areas where the tower coverage is dense, the accuracy will reach 100 m2 (1076 ft 2). In rural areas, the land place will be less accurate, but may still be revealed to the target.
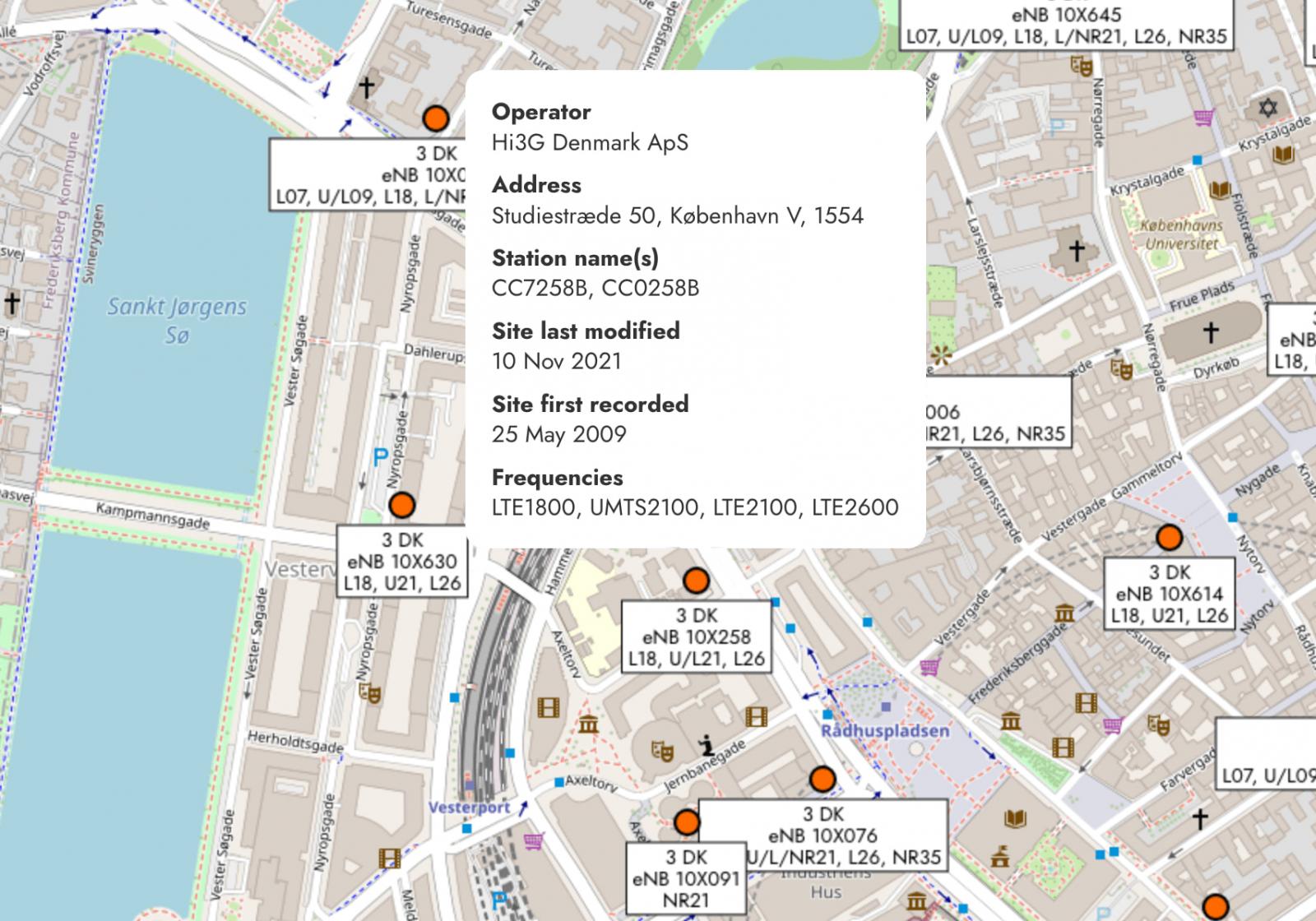
Williams found that when the target was abroad, the trick still worked, as he was located a test topic in Copenhagen, Denmark.
Source: Mastdatabase.co.uk
O2 UK confirms the fix
Williams says that he contacted O2 UK several times on 26 March and 27, 2025, to report his findings, no response.
Finally, he got a direct confirmation from the O2 UK before today that the issue was finalized, and they confirmed it through the test.
In a statement by bleepingcomputer, a virgin media spokesperson confirmed that a fix had been implemented, given that customers do not take any action to protect themselves.
Virgin Media O2 said, “Our engineering teams have been working for several weeks and testing a fix – we can confirm that it is now fully implemented, and tests show that the fix has worked, and our customers do not need to take any action.”
Bleepingcomputer asked O2 whether it was known to exploit this defect and if they plan to inform customers accordingly, but we did not get the reply.



