
The OraCle is warning about an important e-business suit zero-day vulnerability, which allows the attackers to perform informal distance code execution with active exploitation in clop data theft attacks.
The Oracle e-Business Suite (component: BI publisher integration) is within the Oracle concurrent processing product and a CVSS base score of 9.8 due to its lack of authentication and ease of exploitation.
“This safety alert addresses the vulnerability CVE-2025-61882 in the Oracle e-business suit,” reads a new Oracle advisor.
“This vulnerability is exploiting from far away without authentication, that is, it can be exploited on a network without the need for a user name and password. If successfully exploited, this vulnerability can result in distance code execution as a result of this vulnerability.
Oracle has confirmed that zero-day vulnerability affects the Oracle e-business suit, version 12.2.3-12.2.14, and has released one Emergency update To address the defect. The company notes that customers must first install the critical patch updates on October 2023, before they can install new security updates.
As a public POC exploitation exists and the defect is actively exploited, it is important to install security updates as soon as possible for Oracle Admins.
Zero-day exploited in clop data theft attacks
While Oracle clearly did not say that it is a zero-day vulnerability, he has shared the indicators of the compromise that in line with an Oracle EBS exploitation shared by the danger actors on Telegram recently.
Charles Carmacal, CTO, Mandient – Google Cloud, also confirmed that it was a blame exploited by the clop ransomware gang in data theft attacks in August 2025.
Carmakal shared BlappingCompter in a statement, “Clop exploited several weaknesses in Oracle EBS, which enabled them to steal a large amount of data from many victims in August 2025.”
“Many weaknesses were exploited, including the weaknesses, which were in Oracle’s update of July 2025 as well as to patch on the end of this week (CVE-2015-61882),” the Carmacal continued.
CVE-2025-61882 is an important (9.8 CVSS) vulnerability that enables informal distance code execution.
The news of the latest extortion campaign of the clop was broken for the first time last week, when Mandient and Google Threat Intelligence Group (GTIG) reported that they were monitoring a new campaign in which many companies had received emails claiming to be from danger actors.
These emails stated that the clop had stolen data from the company’s Oracle e-business suit system and was demanding ransom not to leak the stolen data.
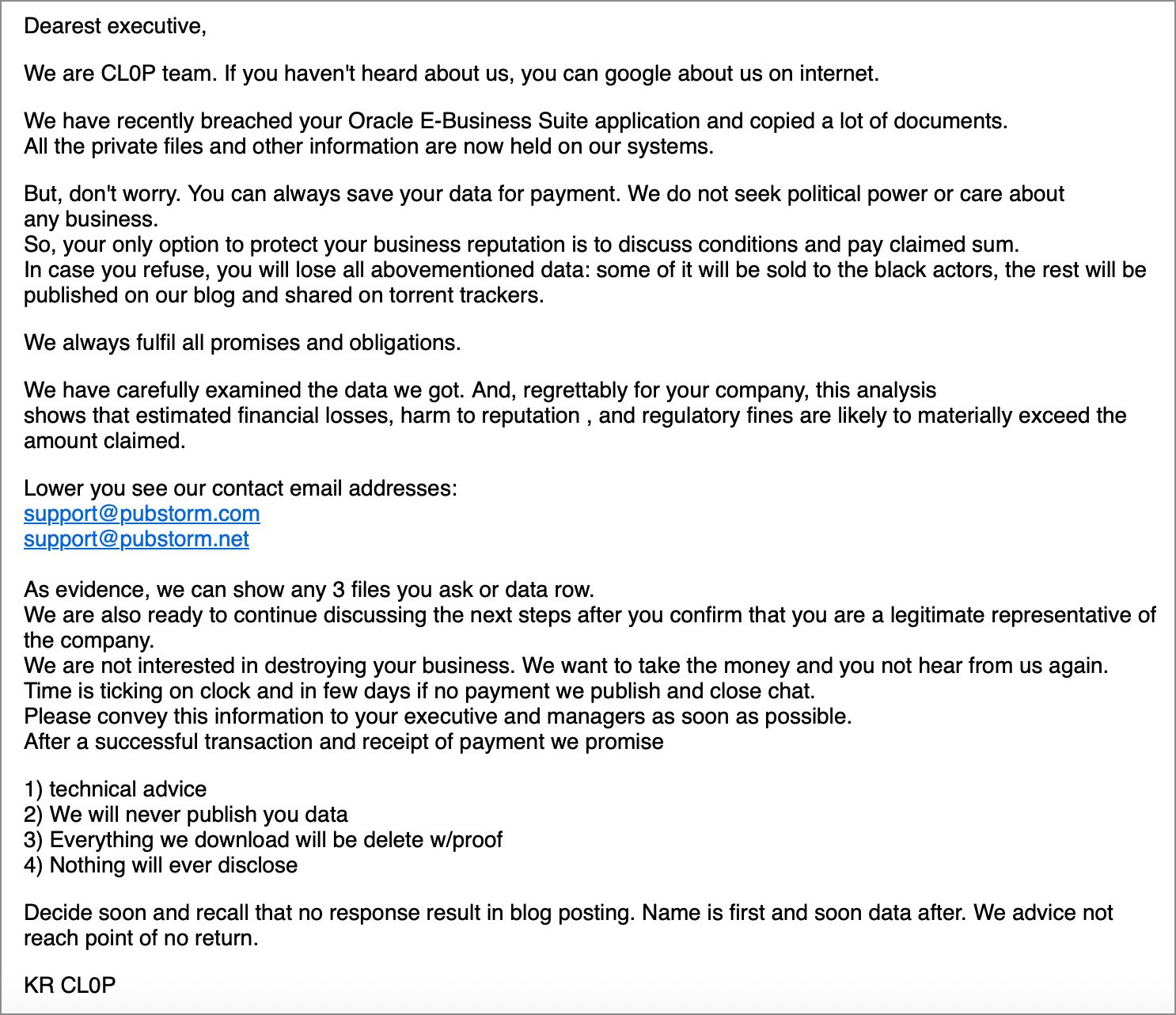
“We are CL0P teams. If you haven’t heard of us, you can go to the internet about us,” reads the forced recovery email shared with bleepingcomputer.
“We have recently violated your Oracle e-Business Suit application and have copied a lot of documents. All private files and other information are now conducted on our system.”
Source: Google
Clop Extortion gang has a long history of exploiting zero-day vulnerability in large-scale data theft attacks, including:
The clop later confirmed the Blapping connecting that he was behind the email of forced recovery and indicated that he exploited an Oracle zero-day vulnerability to steal the data.
Clop told Blapping Copper, “Soon everyone will be clear that Oracle provoked his main product and once again, working on the clop to save the day.”
However, Oracle initially linked the clop extraction campaign to the weaknesses that were patches in July 2025 instead of new zero-days, which we now know that was used in attacks.
Oracle has now shared indicators of agreement for zero-day exploitation, including two IP addresses that exploit the server, a command to open a remote shell, and exploitation collections and related files.
Exploitation leaked by scattered lapsus $ hunter
While clops are behind the theft attacks and the exploitation of Oracle Zero-Day, zero-day reports have come from a separate group of danger actors who are making their headlines recently with their comprehensive data theft attacks on salesforce customers.
On Friday, these actors called themselves “scattered lapsus $ hunters”, as they claim the scattered spider, lapsus $, and the danger actors of shiny -deleters, claiming two files on Telegram, which they said that they belonged to clop attacks.
A file called “Gift_from_Cl0p.7Z” has an ORACLE source code that appears to be related to “Support.oracle.com” based on file names.
However, the danger actors also released a “OraCle_EBS_EXPLIC_POC_POCS_LAPS_LAPS_CL0P_CL0P_Hunters.zip” collection, which he provoked by the file name, which was the Oral e-breach exploitation used by the clop.
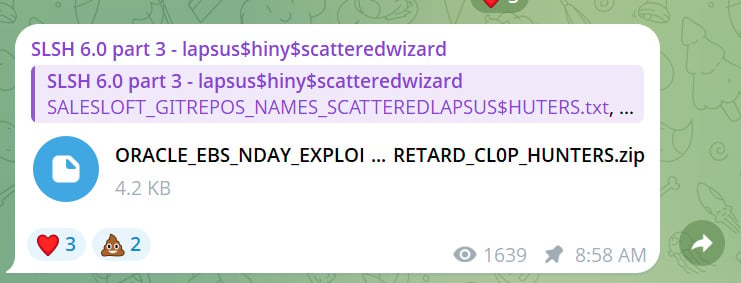
Bleepingcomputer has confirmed that this is the same file listed in the indicators of Oracle’s agreement.
This archives have a readme.MD instruction file and two python scripts, named Exp.Py and Server.py. These python scripts are used to take advantage of a weak oral e-business suit example and either execute an arbitrary command or open a reverse shell on the server of the actor with danger.
List the name of the explight archives shared by Lapsus $ Hunters scattered as IOCS shared by Oracle, now it is confirmed that it is exploitation used by clop ransomware gangs.
However, it raises the question of how the actors of scattered lapsus $ Hunteers have access to exploitation and are they working with clops in some capacity.
Bleepingcomputer contacted both Shinyhunters and representatives of Clop to ask questions about the relationship, but no response was received at this time.



