
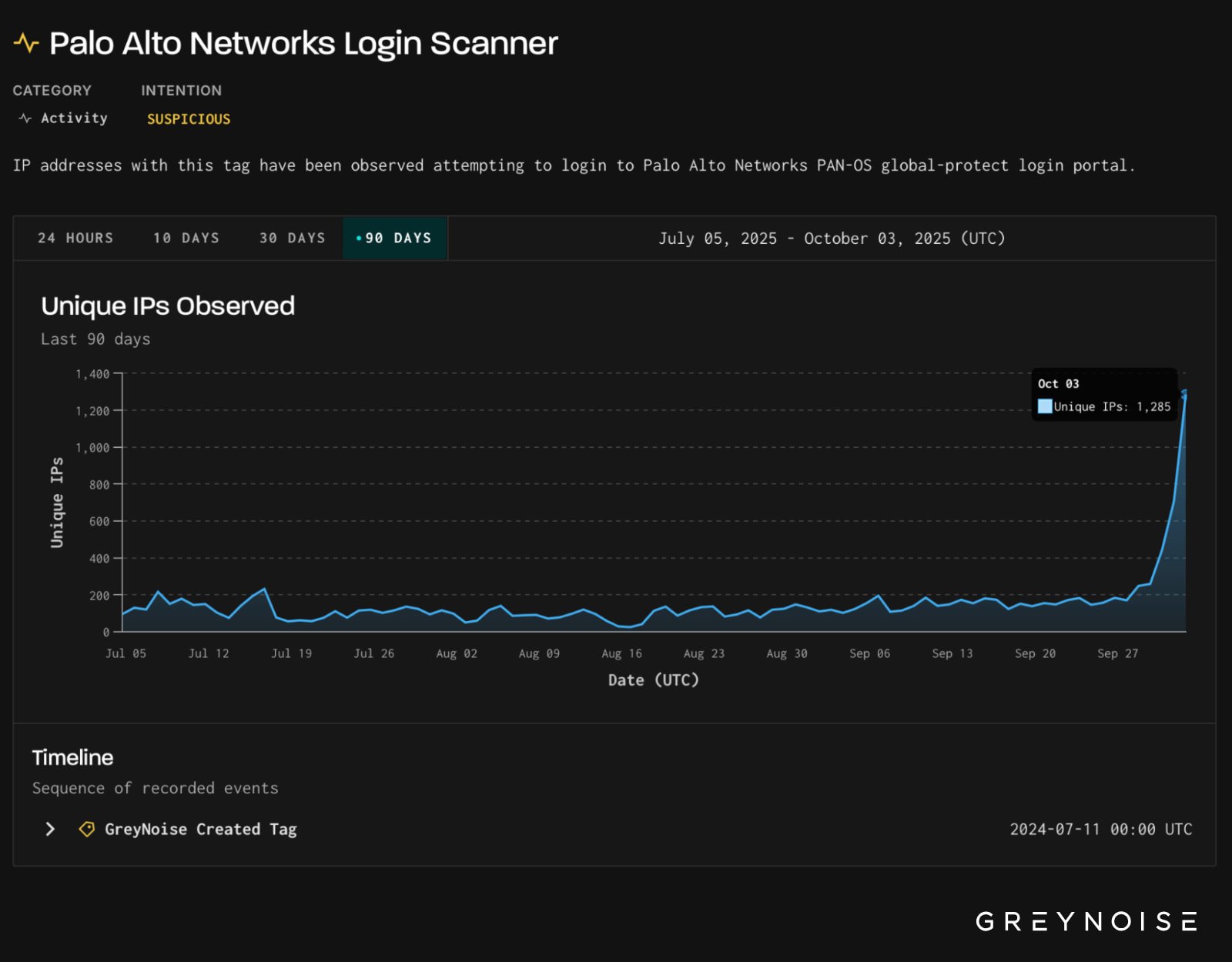
The Palo Alto Network Login Portal indicates a spike in a suspected scan that indicates clear reconnaissance efforts from suspected IP addresses, warning researchers.
Cyber security intelligence company Greynoise Palo Alto Networks reports 500% increase in IP address centered on GlobalProtect and Pan-As profile.
The activity ended on 3 October with more than 1,285 unique IP engaged in activity. Typically, daily scans do not exceed 200 addresses, the company says.
Most viewed IP were geolocated in the US, while small clusters were based in the UK, Netherlands, Canada and Russia.
An activity cluster focuses its traffic on goals in the United States and focuses on another Pakistan, saying that both of them had “separate TLS fingerprints, but not overlap.”
According to GREYNOISE, 91% IP address was classified as suspects. An additional 7% was tagged as malicious.
“Almost all activities were directed on the Palo Alto Profile (Palo Alto GlobalProtect, Palo Alto PAN-OS), which is a granioze, a granioize, suggesting that the activity is targeted in nature, probably obtained from public (eg, shodan, sensor) or attacker-orbalary scan fingerprint, Palo device,” Greynoise explains,
Source: Greynoise
GREYNOISE has earlier warned that such scan activity often indicates the preparation of attacks using new exploits for zero-day or N-Day defects.
The cyber security firm recently issued a warning about an increase in network scans targeting Cisco ASA devices. Two weeks later, news about a zero-day vulnerability came to light in attacks that targeted the same Cisco product.
However, Greenoz states that the correspondence observed for a scan focusing on Palo Alto Network products is weak.
Update 10/5 – Palo Alto Netws made below comment about the comments below to Blapping Campper, which is about Greynoise’s activity:
Security of our customers is always our top priority. We have investigated the reported scanning activity and no evidence of the agreement has been found. The Palo Alto Network is preserved by our own cortex XSIAM platform, which prevents 1.5 million new attacks per day and autonomously reduces 36 billion security events in the most important threats to ensure that our infrastructure remains safe. We are confident in our strong security currency and ability to protect our network. – Spokesperson of Palo Alto Network.
Greffana also targeted
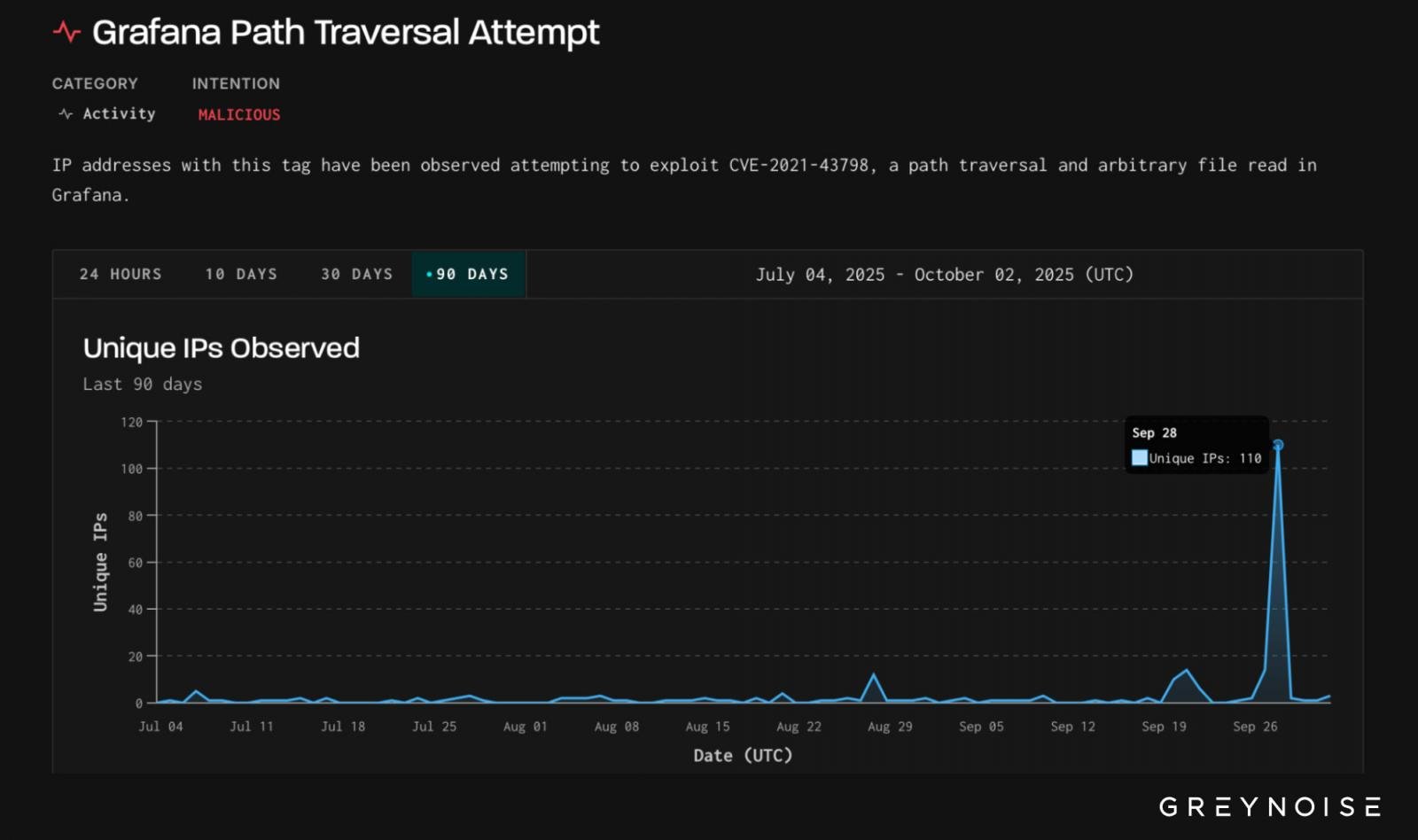
Researchers saw an increase in efforts to exploit an old path traver vulnerability in Grafana. The security issue is identified as CVE-2021–43798 and was exploited in zero-day attacks in December 2021.
Graynoise saw 110 unique malicious IP, most of them start attacks from Bangladesh, from Bangladesh on 28 September.
The goals were mainly based in the United States, Slovakia and Taiwan, maintaining a consistent destination ratio based on specific origin, which usually indicates automation.
Source: Greynoise
GRIYNOISE recommends administrators to ensure that their graphna examples are patches against CVE-2021-43798 and block 110 malicious IP addresses identified.
Researchers have also recommended to check the log for evidence of Path Traversal Requests that may refund sensitive files.



