
Law enforcement officers have demolished a boatnet, which has infected thousands of routers in the last 20 years, to construct two networks of residential proxy, known as any bhelpoxy and 5socks.
The US Department of Justice inspired three Russian citizens (Alexi Victorovic Chertkov, Kiril Vladimirovic Morozov, and Alexandra Alexandrovich Sheshkin) and a Kazakhstani (Dimitri Rabsov) to operate, maintained and involve them in operation with these two illegal services.
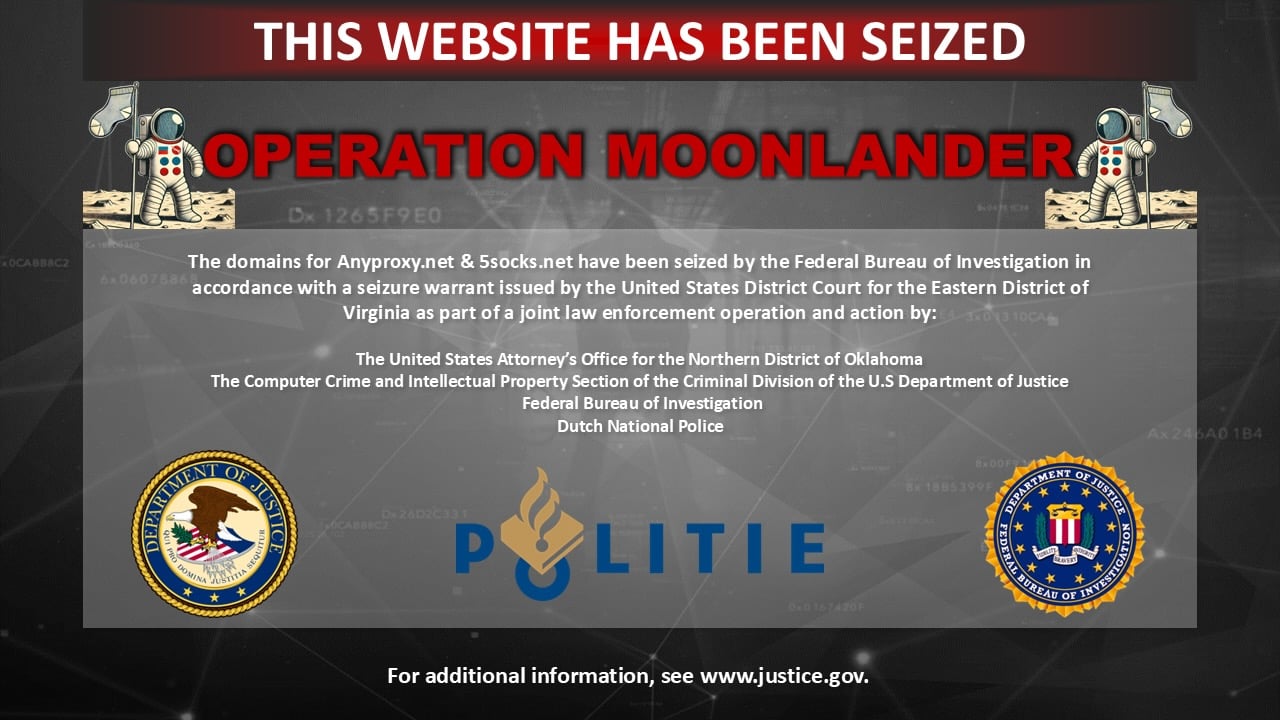
During this joint action, ‘Operation Moonlander’ was dubbed, US authorities worked with prosecutors and investigators with analysts of Black Lotus Labs ‘Black Lotus’, along with the Dutch National Police, Netherlands Public Prosecution Service (Minister of Openbar), and Royal Thai Police.
Court document Show that at least 2004 with malware infected by the old wireless internet router infected botnets worldwide, allowing unauthorized access to unauthorized access to compromised, which can be sold as a proxy server on any hungry and 5socks.net. Both the domains were managed by the Virginia -based company and hosted on the server globally.
“Botate controllers require cryptocurrency for payment. Users are allowed to connect directly with proxy using without any authentication, which in previous cases can get free access to a comprehensive spectrum of malicious actors,”. Black Lotus Labs said,
“Given the source range, only 10% is found only 10% as malicious in popular devices such as wirestottal, which means that they avoid network monitoring tools with constant high levels of success. Such prauxies have been designed to hide advertisement, DDOS attacks, creut forces, or a series of illegal activities about the victims.
Their users paid monthly membership from $ 9.95 to $ 110 per month, based on requested services. The Department of Justice said, “The slogan of the website has been working since 2004! Where did you say today,
Four defendants advertised two services (promoted more than 7,000 proxy) as residential proxy services on various websites, including people used by cyber criminals, and allegedly collected more than $ 46 million from selling memberships of Anniprox Botnet’s infected routers share.
He operated Anyproxy.net and 5socks.net websites using a Russian Internet hosting provider, registered and hosted in JCS Fedora Communications. He also used the server to manage any botnet and two websites in other places in the Netherlands, Türkiye, and other places.
All of them were accused of conspiracy and damage to protected computers, while Chertkov and Rubtsov were also accused of registering a domain name.
Targeting and-Life (EOL) Router
On Wednesday, the FBI also warned the announcement of a flash consultant and a public service that the Botet Patch End-Life (EOL) was targeting the routers with a version of Thomoon Malware.
The FBI warned that the attackers are later installing the proxy used to detect cyber crime-for-hier activities, cryptocurrency theft attacks and other illegal operations.
The list of target devices by Botnett includes Linnas and Cisco router models, including:
- Linksys E1200, E2500, E1000, E4200, E1500, E300, E3200, E1550
- Linksys WRT320n, WRT310N, WRT610N
- Cisco M10 and Cradalpoint E100
“Recently, with some routers, remote administration at the end of life, along with turning on, a new version was compromised by a new version. This malware allows cyber actors to install proxy on the afflicted router and conduct cyber crimes,” said the FBI.
“Such residential proxy services are especially useful for criminal hackers, providing oblivion when doing cybercrime; residential-commercials usually consider by residential-IP addresses usually by internet security services, as it is more likely to have legitimate traffic,” said in today’s prosecution. “Thus, conspirators received a personal financial benefit from the sale of access to the compromised routers.”



