
A new large-scale botnet called Rondodox is targeting 56 vulnerabilities in more than 30 different devices, including flaws first revealed during Pwn2Own hacking competitions.
The attacker focused on a wide range of exposed devices including DVRs, NVRs, CCTV systems and web servers and has been active since June.
The Rondodox botnet takes advantage of what Trend Micro researchers call an “exploit shotgun” strategy, where multiple exploits are used together to maximize infection, even if the activity is very noisy.
since FortiGuard Labs Discovers RondodoxThe botnet appears to have expanded the list of exploited vulnerabilities, including CVE-2024-3721 and CVE-2024-12856.
Large scale N-day exploitation
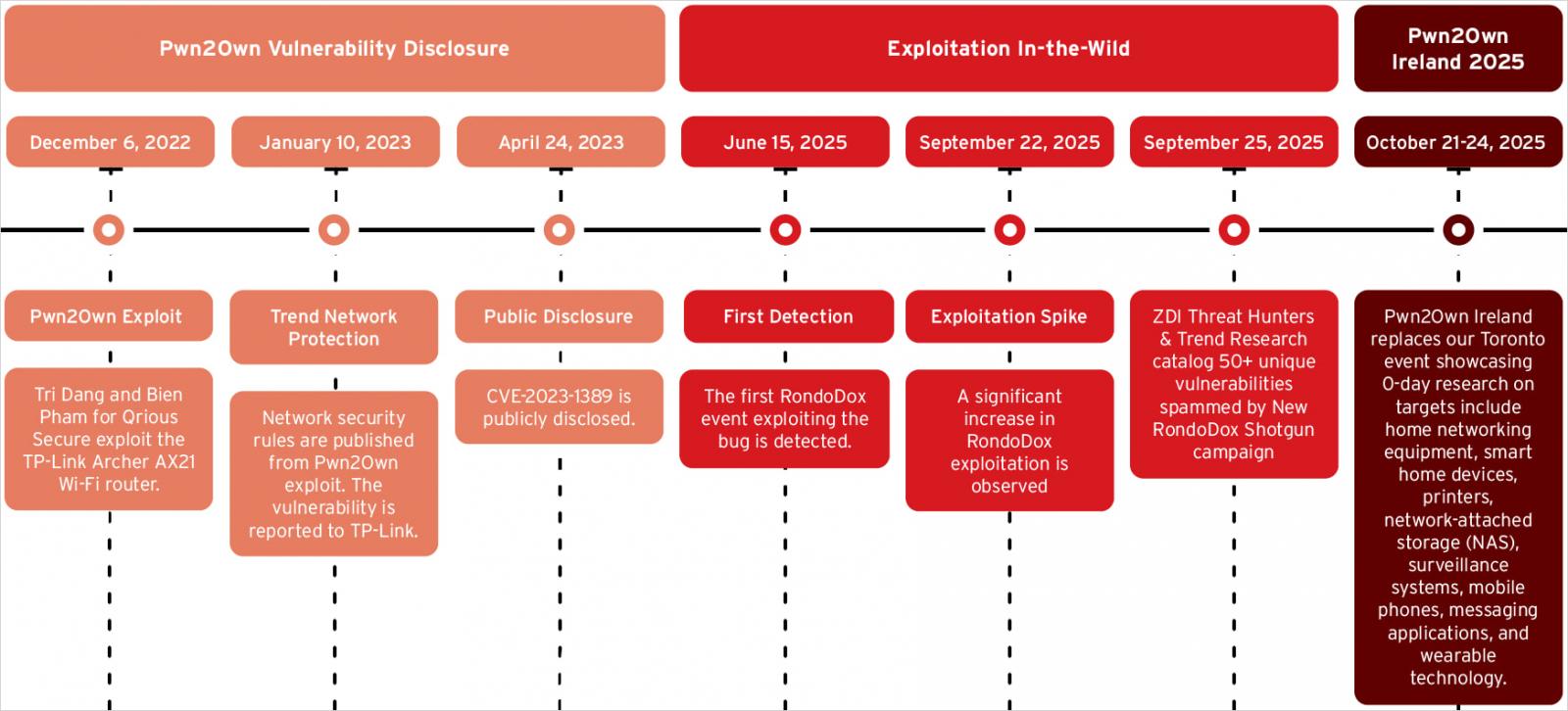
one in report Today, Trend Micro says Rondodox exploits CVE-2023-1389, a flaw in the TP-Link Archer AX21 Wi-Fi router that was originally revealed at Pwn2Own Toronto 2022.
Pwn2Own is a hacking competition held twice a year by Trend Micro’s Zero Day Initiative (ZDI), where white-hat teams demonstrate exploits for zero-day vulnerabilities in widely used products.
Source: Trend Micro
Security researchers note that botnet developers pay close attention to exploits exposed during Pwn2Own incidents, and move quickly to weaponize them, as Mirai did in 2023 with CVE-2023-1389.
Below is a list of post-2023 N-Day faults that Rondodox has added to its arsenal:
- Digivar – CVE-2023-52163
- QNAP – CVE-2023-47565
- LB-Link – CVE-2023-26801
- TrendNet – CVE-2023-51833
- D-Link – CVE-2024-10914
- TBK – CVE-2024-3721
- char-faith – CVE-2024-12856
- Netgear – CVE-2024-12847
- Avitek – CVE-2024-7029
- Totolink – CVE-2024-1781
- Tenda – CVE-2025-7414
- Totolink – CVE-2025-1829
- MeteorBridge – CVE-2025-4008
- Edimax – CVE-2025-22905
- Linksys – CVE-2025-34037
- Totolink – CVE-2025-5504
- TP-Link – CVE-2023-1389
Old faults, especially in devices that have reached end of life, are a significant risk as they are more likely to be unfixable. Having the latest in supported hardware is equally dangerous as many users ignore firmware updates after setting up the device.
Trend Micro also found that Rondodox contains exploits for 18 command injection flaws that have not been assigned a vulnerability ID (CVE). They affect D-Link NAS units, TVT and Lilin DVRs, FiberHome, ASMAX and Linksys routers, BRICCOM cameras, and other unknown endpoints.
To protect against RondoDox and other botnet attacks, apply the latest available firmware updates for your device and change the EOL device. It is also recommended to partition your network and replace default credentials with secure passwords to isolate critical data from Internet-facing IoTs, or guest connections.



