
Microsoft has warned that a cyber-jusnic group associated with Russia’s Federal Security Service (FSB) is targeting diplomatic missions in Moscow using local internet service providers.
The hacking group (also known as Turla, Waterbug, and toxic Bear), which has been tracked by Microsoft as a secret icy storm, has been seen exploiting the status of its opposing-in-in-middle (ISP) level at the Internet Service Provider (ISP) level, which collects political missions with custom apo-pollware.
To do this, they redirect the goals for captive portals, tricking them to download and execute the malware payload, disguised as a Kasperki antivirus update, which installs a reliable root certificate.
Once deployed, apoloshao helps to trick the equipment compromised to recognize malicious websites as valid, allowing danger actors to maintain long -term access to intelligence after infiltration into diplomatic systems.
“This is the first time that secret urgency can confirm the ability of secret icy storm to spy at the Microsoft ISP level, which means that local internet providers in Russia and diplomatic personnel using telecommunications in Russia are at risk of the target of Aitm status of secret urgency within those services,” Microsoft said.
“This campaign, which has been running since at least 2024, creates a high risk for foreign embassies, diplomatic institutions and other sensitive organizations working in Moscow, especially for institutions that trust local internet providers.”
While Microsoft first discovered the attacks in February 2025, the company believes that this cyber-grooming campaign is active since at least 2024.
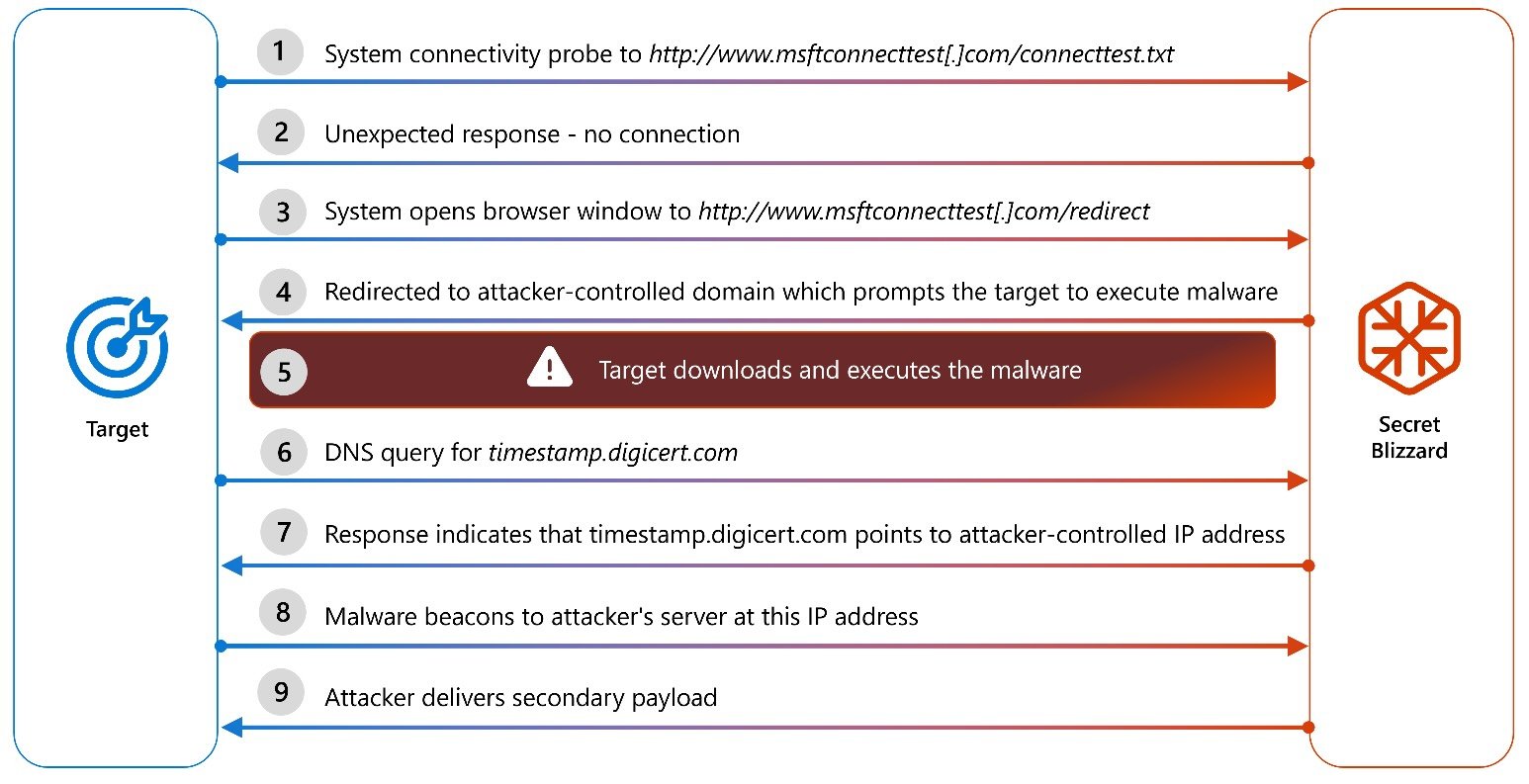
There are also secret blizzard hackers Taking advantage of Russia’s domestic obstruction systemsIncluding the system for operative investment activities (SORM) to complete their large -scale AITM campaigns.
Unconventional cyberspace focusing on high-profile goals
Turla has been orchestrated on cyber-justification and information theft operations targeting embassies, governments and research facilities in more than 100 countries since at least 1996.
Two years ago, CISA Joined together The Center of the Center on 16 of Russia’s Federal Security Service (FSB) and a Peer-to-Pier (P2P) network, which is a network of computers infected with snake cyber-jusnual malware, which was later taken down in a joint action associated with five-eye cyber security and intelligence agencies.
These Russian state -backed hackers are also primary suspects behind target attacks. US Central Command, NASA, PentagonMany Eastern European Foreign Ministry, Finnish MinistryAnd European Union governments and embassies.
This danger group is known for its unconventional strategy, including control of malware through the comments of Brittany Spears on Instagram photos and the use of backdoor Trojan with its own API.
Turla also used the kidnapped infrastructure and malware of the Iranian APT Oilrig in their own campaigns to hold the Iranian state hackers responsible for their attacks.
Recently, he has been seen kidnapping the infrastructure of Pakistani threats Hurricane -0156 to target Ukrainian military equipment connected through Starlink.



