
A wave of data violations affecting companies such as Qantas, Allianz Life, LVMH, and Adidas has been forcibly connected to the recovery group, which is using voice phishing attacks to steal data from SAlesforce CRM examples.
In June, Google’s Threat Intelligence Group (GTIG) warned that the danger actors tracked as UnC6040 had targeted salesforce customers in social engineering attacks.
In these attacks, the danger actors applied the IT support staff to the target employees in phone calls, making them an attempt to visit the connected app setup of the salesfors. On this page, he was asked to enter a “connection code”, which connected a malicious version of the Slesforce’s data loader Oauth app to the target salesfores environment.
In some cases, the data loader component was converted into a “My Ticket Portal”, so that the attacks could be more confident.
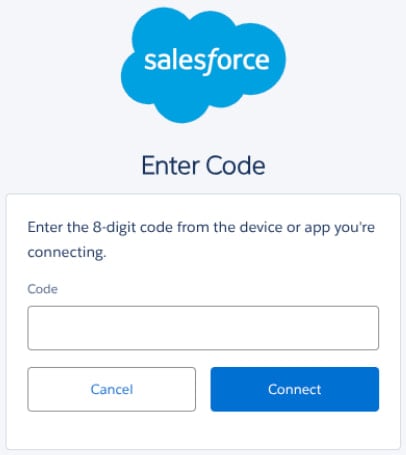
Source: Google
The GTIG says that these attacks were usually carried out through Voice Fishing, but credentials and MFA tokens were also stolen through the fishing pages that applied Oxta login pages.
At the time of this report, many companies reported data violations related to third-party customer service or cloud-based CRM system.
LVMH assistant Tiffany & Co. Each revealed unauthorized access to customer information database Tiffany Korea informs customers The attackers violated the “seller forum used for managing customer data”.
Adidas, Kantas and Allianz Life also reported violations involving third-party systems, in which Eliyanz confirmed that it was a third-party customer relationship management platform.
“On July 16, 2025, a malicious danger actor achieved access to a third-party, cloud-based CRM system used by Elianz Life Insurance Company (Allianz Life) in North America,” a spokesperson of an Allians Life reported to the BlappingComer.
While Bleepingcomputer has learned that Qantas Data Breach also included a third-party customer relationship management forum, the company would not confirm that it is salesforce. However, Previous reporting Local media claims that data was stolen from Qantas’s salesforce example.
In addition, court documents stated that the danger actors targeted “accounting book” And “Contact“The database table, both salesforce objects.
While none of these companies have publicly named salesforce, Bleeping Computer has since confirmed that all were targeted in the same campaign detailed by Google.
The attacks have not yet led public forcibly recovery or data leaks, in which Blapping communal is to learn that the actor of danger is trying to exclude companies privately on email, where they name themselves as shiny.
It is believed that when these forced recovery efforts fail, the danger actor will release information about the theft in the leak of leaks, which is similar to the previous snowflake attacks of the shinhunter.
Who is shiny
Violations have created confusion between the cyber security community and the media, including the blapingCopper, attached to the spider scattered with attacks (tracked by the mandient as UnC3944), as those danger actors were also targeting aviation, retail and insurance areas around the same time and demonstrated similar strategies.
However, actor with scattered spider-related danger performs fully developed network violations, closing with data theft and sometimes, ransomware. On the other hand, shinyhunters tracked as UNC6040, go to focus more on data-chori extortion attacks targeting a particular cloud platform or web application.
This includes overlapping members in both UNC6040 and UNC3944 who communicate within the same online communities. The threatening group is also believed to be overlap with “The Com”, a network of experienced English -speaking cyber criminal.
Alan Licca, an intelligence analyst for the recorded future, said, “According to future intelligence, overlapping TTPs indicate some crossover between two groups, amidst the attacks of known scattered Spider and Shinoors.
Other researchers have told Bleepingcomputer that the shinyers and the scattered spider are seen working in the lockstap, targeting the same industry at the same time, making it difficult to characterize the attacks.
Some also believe that the two groups now have a threat to the actors from the Lepsus $ Hacking Group, showing the report that it was one of the recently arrested Spider Hackers Also in lapsus $,
Another theory is that shinniyas are acting as a forced recovery, where they take out companies on behalf of other danger actors in exchange for revenue stake, similarly how the Rainsware-e-A-Sarvis gangs operate.
The principle is supported by previous interaction, BlappingCopper has done with Shainhemers, where he claimed that there is no violation, but is just working as a seller of stolen data.
These violations include Povers School, Oracle Cloud, The Snowflake Data-Chori Attack, AT & T, NitropDF, Watpad, Mathway and many more.
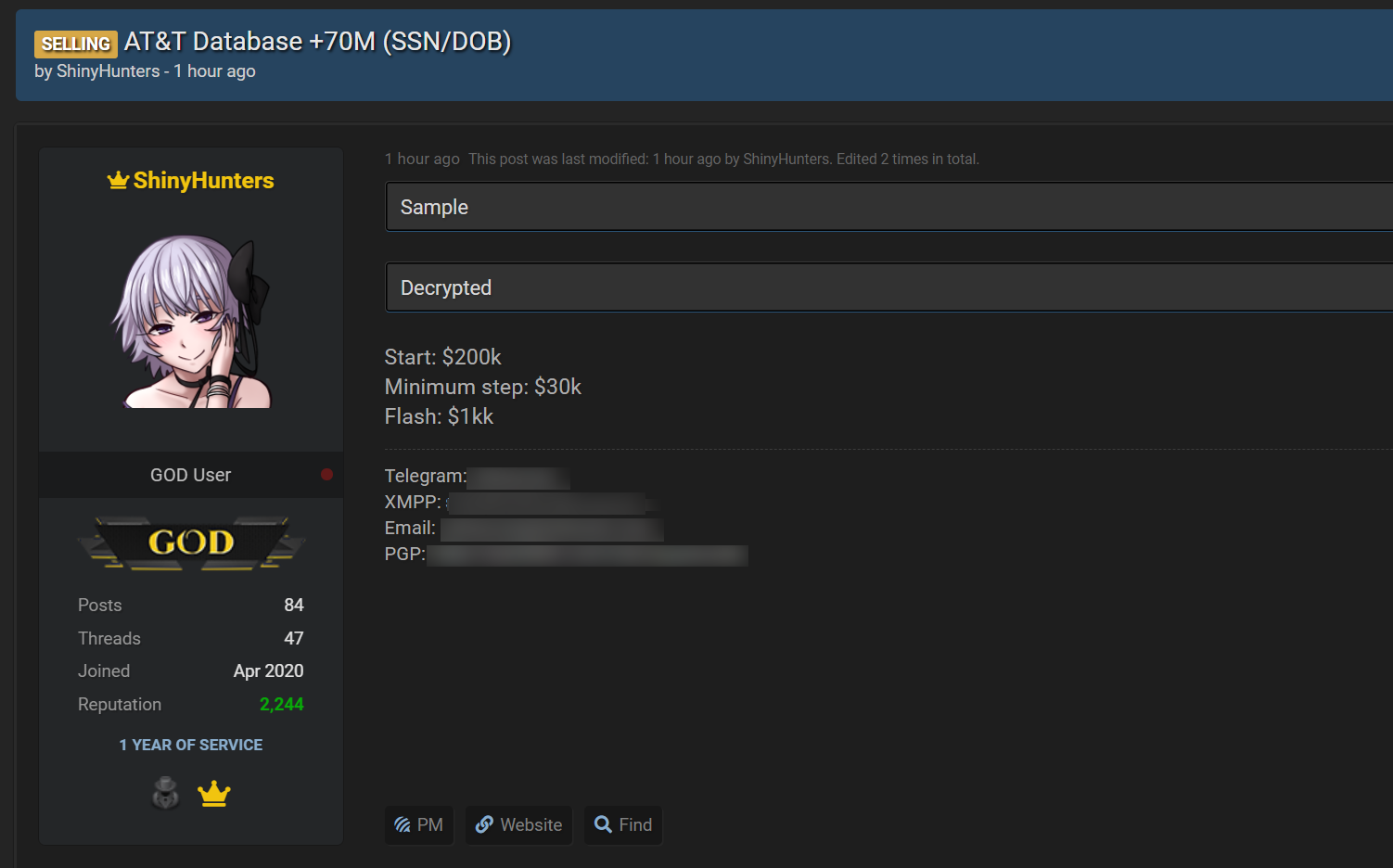
Source: Bleepingcomputer
To make the water more scavenging, there have been several arrests of people associated with the name “Shainheters”, including snowflake data-chori attacks, are involved in the operation of violations and violated V2 hacking forums in the powerscool.
Nevertheless, even after these arrests, forcibly recovering emails with new attack companies, “We are shiny,” refer to themselves as “collectives”.
Protect salesforce examples from attacks
In a statement by Bleepingcomputer, Salesforce insisted that the platform was not compromised on its own, but, the accounts of the customers are being dissolved through social engineering.
“सेल्सफोर्स से समझौता नहीं किया गया है, और वर्णित मुद्दे हमारे प्लेटफॉर्म में किसी भी ज्ञात भेद्यता के कारण नहीं हैं। जबकि सेल्सफोर्स हम जो कुछ भी करते हैं, उसमें एंटरप्राइज-ग्रेड सुरक्षा का निर्माण करता है, ग्राहक भी अपने डेटा को सुरक्षित रखने में एक महत्वपूर्ण भूमिका निभाते हैं-विशेष रूप से परिष्कृत फ़िशिंग और सोशल इंजीनियरिंग हमलों में वृद्धि के बीच,” सेल्सफोर्स ने ब्लेपिंगकॉम्पटर को बताया।
“We continue to encourage all customers to follow the best practices, including to enable multi-factor authentication (MFA), implementing the principle of at least privileges, and managing carefully associated applications. For more information, please see: https://www.salesforce.com/blog/protect-gainst- social- enginering/,
Salesforce urges customers to strengthen their safety currency:
- Implementing reliable IP range to login
- After the principle of at least privileges for app permissions
- Multi-Faculty certification enabled (MFA)
- Connecting apps and managing access policies
- Using Salesforce Shield for advanced danger, event monitoring and transaction policies
- Adding a specified safety contact to the event communication
The details about these mitigations and the details above can be found under the guidance of the salesforce.



