
A new attack that is dubbed ‘Smartattack’ uses Smartwatches as a secret ultrasonic signal receiver, which exfers data from an air-gap system.
Usually mission-mating environment such as government facilities, air-gapped systems deployed in weapons platforms and nuclear power plants are physically isolated from the outer network to prevent malware infections and data theft.
Despite this isolation, they are insecure to compromise through internal dangers such as USB drives or state-proposed supply chain attacks.
Once the infiltration, the malware can operate secretly, using secret techniques to modify the physical characteristics of the hardware components to transmit sensitive data to the nearby receiver without interfering with regular operation of the system.
Smarttac was prepared by researchers at the University of Israeli Mordakai GuriA specialist in the field of secret attack channels, who previously presented ways to leak data using LCD screen noise, RAM modulation, network card LED, USB drive RF signal, SATA cable and power supply.
While attacks on the air-gapped environment, in many cases, are the theoretical and extremely difficult to achieve, they still introduce interesting and novel approaches to exfiltrate data.
How SmartTac works
Smartattack somehow requires malware to infect an air-gapped computer to collect sensitive information like Kestrokes, Encryption Keys and Credentials. This can then be used by a computer underlying speaker to emit ultrasonic signals to the environment.
Using binary frequency shift king (B-FSK), audio signal frequencies can be modified to represent binary data, aka and zero. The frequency of 18.5 kHz represents “0”, while 19.5 kHz “1.” It reflects.
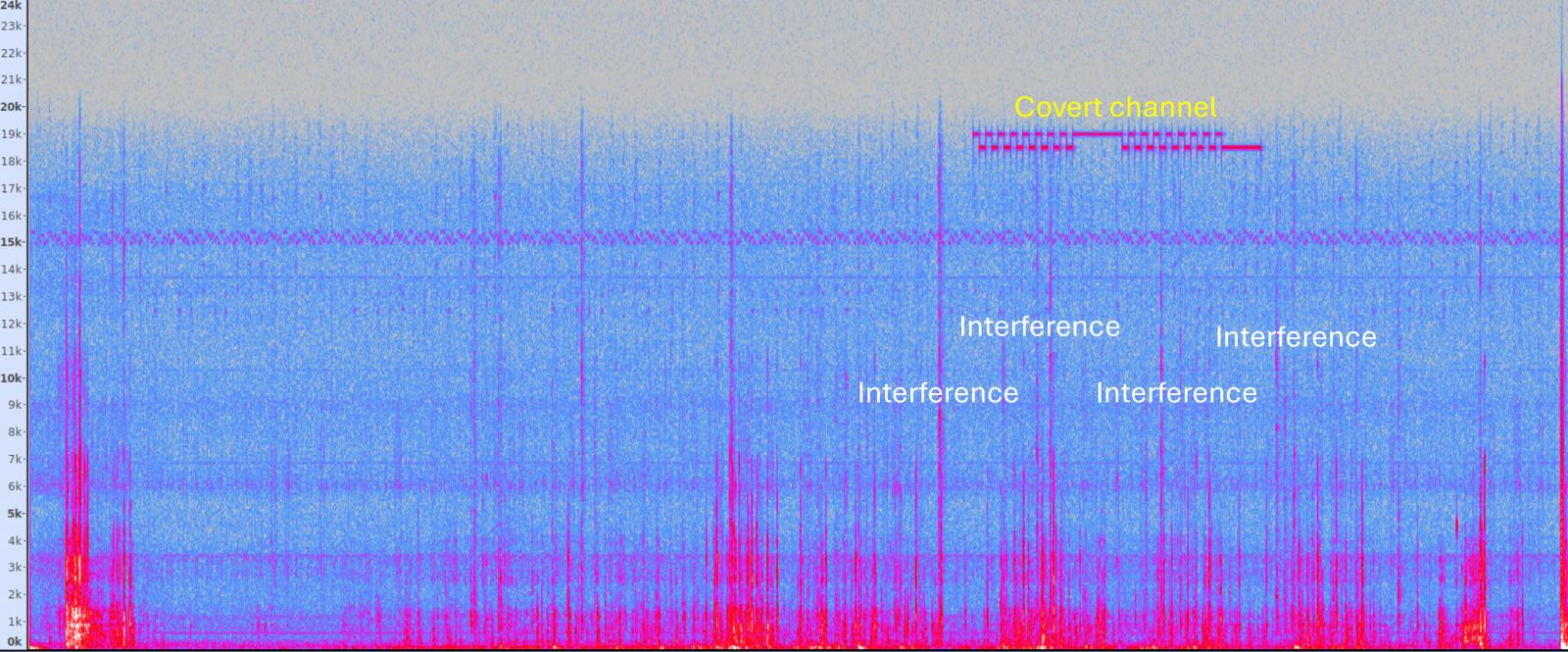
Source: Arxiv.org
In this range, frequencies are inaccessible to humans, but they can still be caught by a smartwatch microphone worn by a person nearby.
The sound monitoring app in the smartwatch applies a signal processing technique to detect the frequency shift and demodulate an encoded signal, while integrity testing can also be applied.
The final exfiltration of data can occur through Wi-Fi, Bluetooth or cellular connectivity.
Smartwatch can either be either equipped with an evil employee from this device, or outsiders can infect it without the knowledge of the wearer.
Demonstrations and limitations
Researchers noted that smartwatch uses smaller, low-SNR microphones than smartphones, so signal demodulation is quite challenging, especially on high frequencies and low signal intensity.
Even wrist orientation was found to play an important role in the viability of the attack, when the clock was the best work when the clock was “line-of-vision”.
Depending on the transmitter (speaker type), the maximum transmission range is between 6 and 9 m (20 – 30 ft).
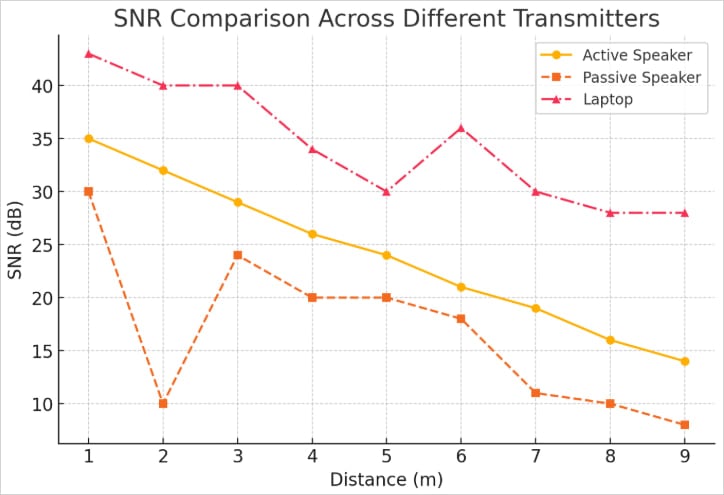
Source: Arxiv.org
The data transmission rate ranges from 5 bits per second (BPS) to 50 bps, which reduces reliability in the form of increase in rate and distance.
.jpg)
Source: Arxiv.org
Researchers say that the best way to combat smarttacks is a ban on using smartwatch in a safe environment.
Another solution would be to remove in-built speakers from air-gapdi machines. This will eliminate the surface of the attack for all acoustic secret channels, not just smartattack.
If none of this is possible, ultrasonic jamming can still prove to be effective through broadband noise, software-based firewall and audio-gaping emissions.



