
Researchers have found that in about 80% of cases, spikes are a precursor for the disclosure of new security weaknesses (cves) within six weeks in malicious activity such as networks, targeted scannings, and brutal-founding efforts.
This danger monitoring firm is discovered by Greenois, which reports that these events are not random, but are characterized by repeated and statistically important patterns.
On the data of its ‘Global Observation Grid’ (GOG) collected from September 2024, Greynoise made it the basis, the objective to avoid the result-contemporary cherry-picker applied to statistical threshold.
After removing noise, vague and low quality data, the firm ended with 216 phenomena, which were qualified as spike events, tied to eight enterprise edge vendors.
“We studied during all 216 spike events, a new CVE within three weeks after 50 percent, and 80 percent within six weeks,” Explain researchers,
The correlation was particularly stronger for Ivanti, Sonicwall, Palo Alto Network, and Fortinet products, and was weak for Mikrotic, Citrix and Cisco. State-provided actors have repeatedly targeted such systems for early reach and perseverance.
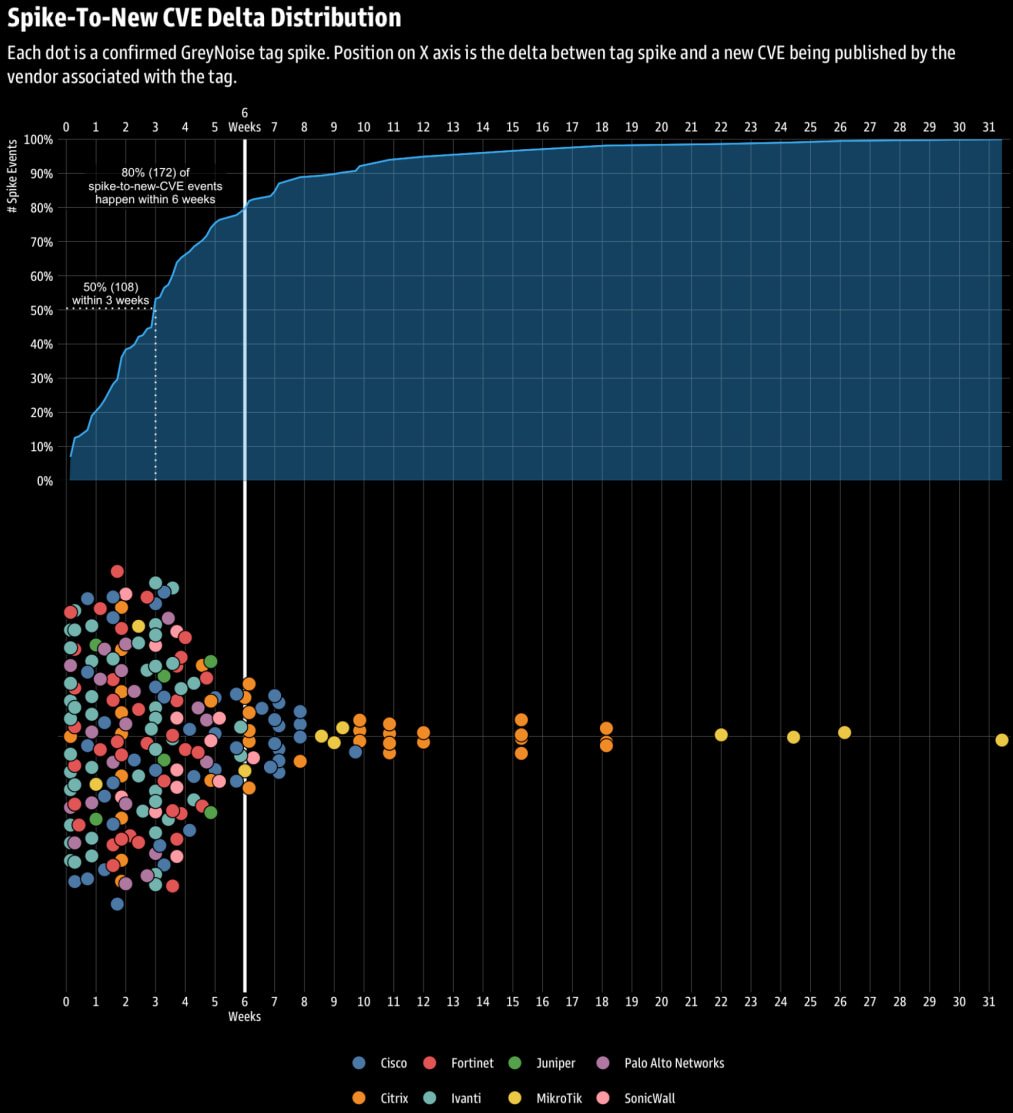
Source: Greynoise
Greynoise notes that in most of the underlying cases in these spikes, attackers demonstrate exploitation efforts against old, known flaws.
Researchers believe that it facilitates either the discovery of new weaknesses or the discovery of the internet-desired closing points that can be targeted in the next stage of the attack, which take advantage of the novel adventures.
A “My Canary”
Traditionally, defenders respond after a CVE is published, but the findings of Greenois suggest that the attacker behavior may be a major indicator and a tool for active rescue organizing.
These pre-pronounced spikes give defaults a window to prepare, increase monitoring, and prepare a harden system against a possible attack, even if no security updates protect them and they do not know which system component or function is actually targeted.
Greynoise recommends that scanning activity can be closely monitored and the original IPS is immediately blocked, as it makes them out of reconnaissance that usually leads to real attacks.
Researchers have been underlined that these cases should be expected to scan for chronic flaws, as the attackers aim to list those assets. Therefore, those people should not be disregarded as failed attempts to break the fully painted closing points.
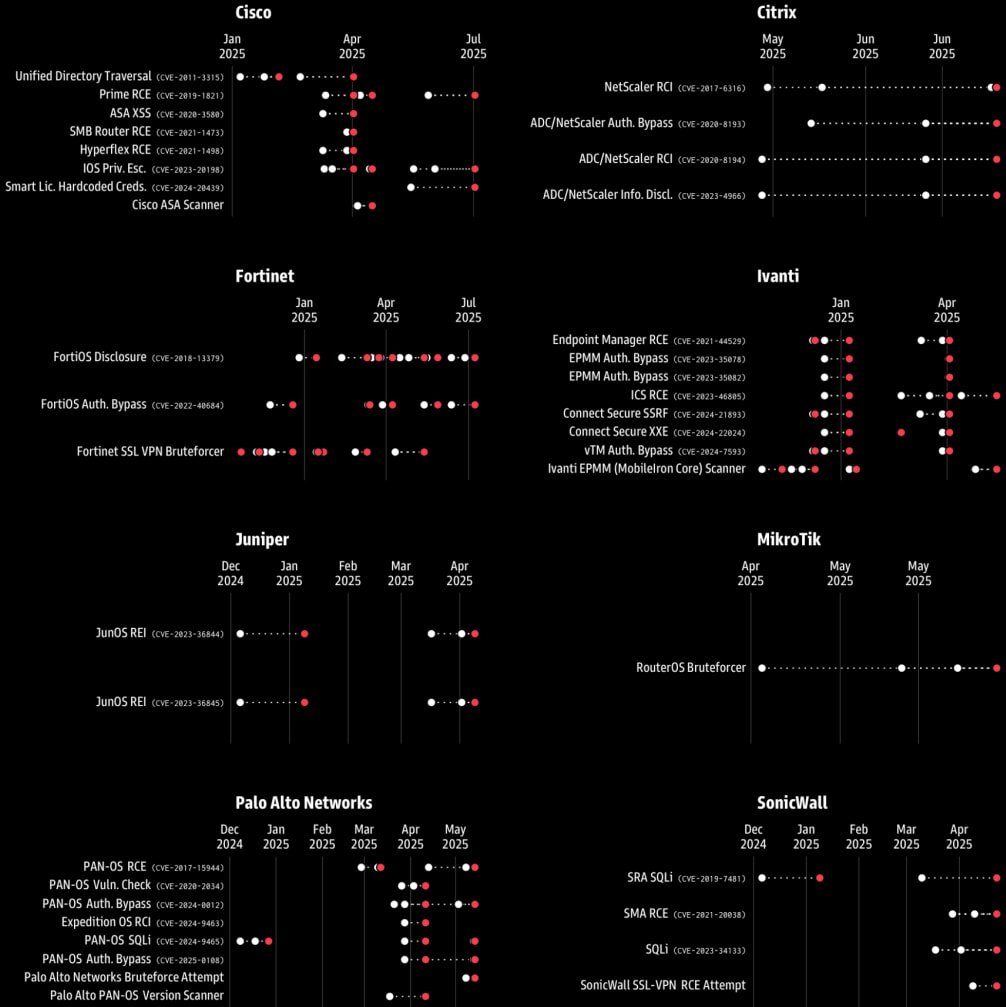
Source: Greynoise
On related development, google Project Zero declared This will begin to inform the public that a vulnerability has been discovered within a week, which helped the system admins to increase their defense, while the sellers work on developing a patch.
Project Zero will now share new defects, discovery time and disclosure deadline (still in 90 days), the seller/project and product.
Technical details, proof-of-concept exploits, or reducing any other information that can tip the attackers, hope that this change will have no adverse effects on security, while will help reduce the “patch gap” at the same time.



