
A widely used information steeler and malware downloader, steel creators have released their second major version, with many secrets and data theft enhancement.
The latest version of Stealc was actually made available to the cyber criminal in March 2025, but Zscaler researcher Those who analyzed it published only one detailed writing.
In the weeks after its release, many minor bug fixes and point releases added new features, with the latest version 2.2.4.
Stealc is a mild information-chori malware that received traction on the dark web in early 2023, selling access for $ 200/month.
In 2024, it was seen in large -scale maltizing operations and the locking system was attacked.
In the late 2024, it was confirmed that SteelC’s development remained very active, its developers allowed Chrome’s ‘app-bound encryption’ to add a mechanism to cookie-and-door defense, allowing the “regeneration” of cookies to hijack Google accounts.
New in the latest version
Version 2 (and later) was announced in March 2025. According to ZSCAler’s analysis, it brings the following major improvements:
- Palor delivery enhancement with exe files, MSI package, and powerrashell script, and supportable payload trigger.
- The RC4 encryption code strings and command-end-control (C2) were added to communication, with random parameters in C2 reactions for better theft.
- Improvement in architecture and execution with new payload compiled for 64–bit systems, dynamically resolves API functions on runtime, and introduces a self-disconnection routine.
- The new embedded builder that allows operators to generate new Stealc builds using templates and custom data theft rules.
- Telegram bot support was added for real -time alerts for operators.
- The capacity was added to screenshots the victim’s desktop with multi-monitor support.
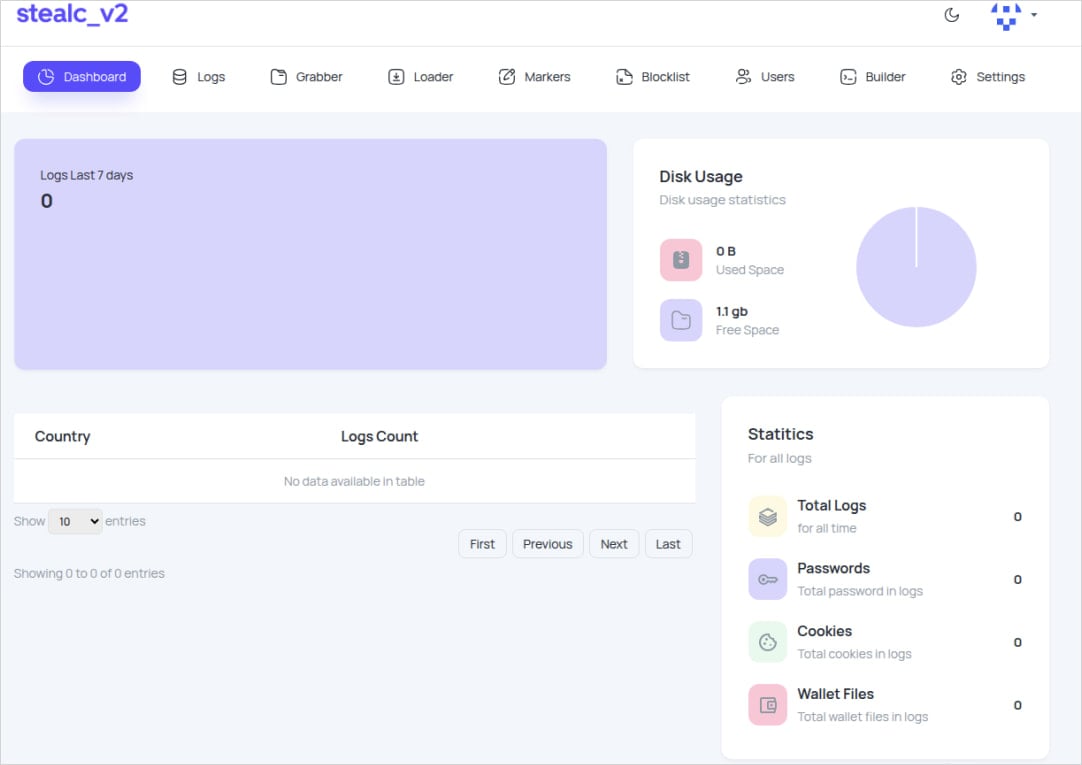
Source: Zscler
However, in addition to feature additions, some remarkable expulsions have also occurred, such as anti-VM checks and DLL downloading/execution.
These may indicate an effort to create malware lenters, but they can also cause collateral damage from the major code rear and can be better reprinted in future versions.
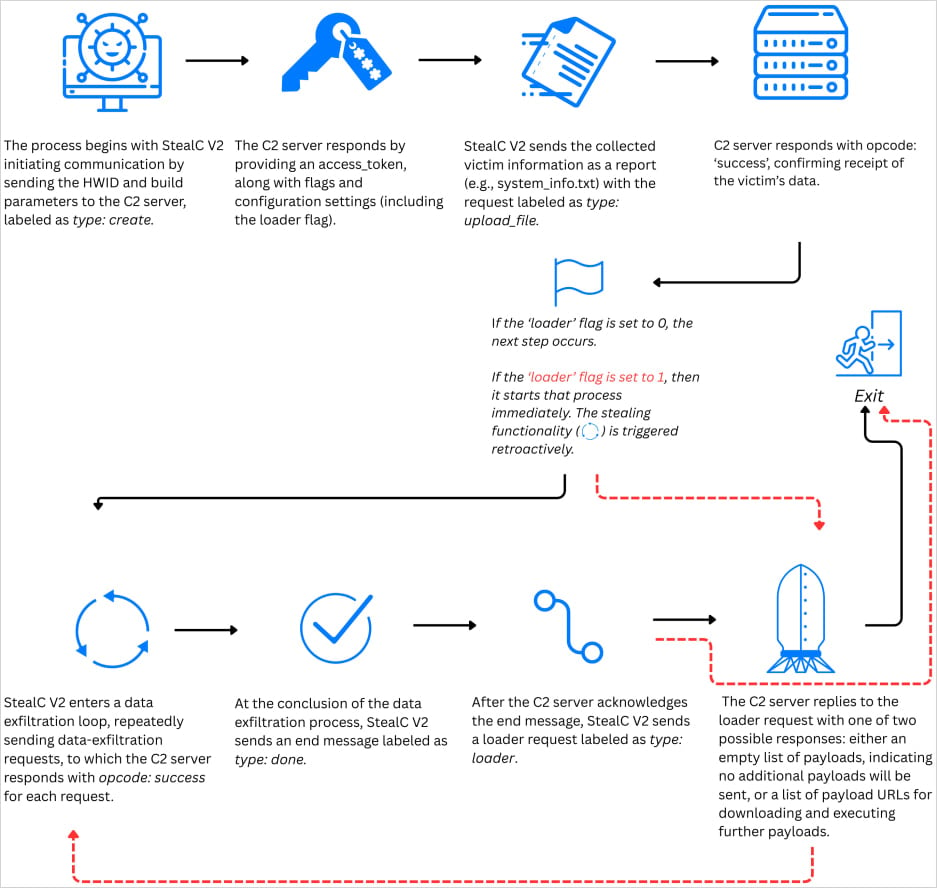
Source: Zscler
In the most recent attacks viewed by ZSCAler, Stealc was deployed by amadey, a separate malware loader, although separate operators can separate delivery methods or attack chains.
To protect your data from informing malware, avoid storing sensitive information on your browser for convenience, use multi-factor authentication to protect your accounts, and never download pirated or other software from unclear sources.



