
An NPM package called ‘Rand-User-Ecent’ has been compromised in a supply chain attack to inject objected codes that activate a remote access to a user on the user’s system.
,Rand-user-agent‘Package is a device that produces random user-agent strings, which is helpful in web scrapping, automatic testing and safety research.
Although the package has been removed, it is quite popular, the average 45,000 download weekly.
However, according to researchers AcidoThreatening actors took advantage of their semi-finished popular status to inject malicious codes in unauthorized subsequent release, which is likely to be downloaded by a significant number of downstream projects.
Aikido discovered the agreement on May 5, 2025, when its malware analysis system marked a new version of Rand-Rand-Egent, number 1.0.110.
On intensive examination, the researchers found the hidden code in the ‘D from’ D from/Index.JS ‘, which was only visible when the user scrolls horizontally in the source scene on the NPM site.
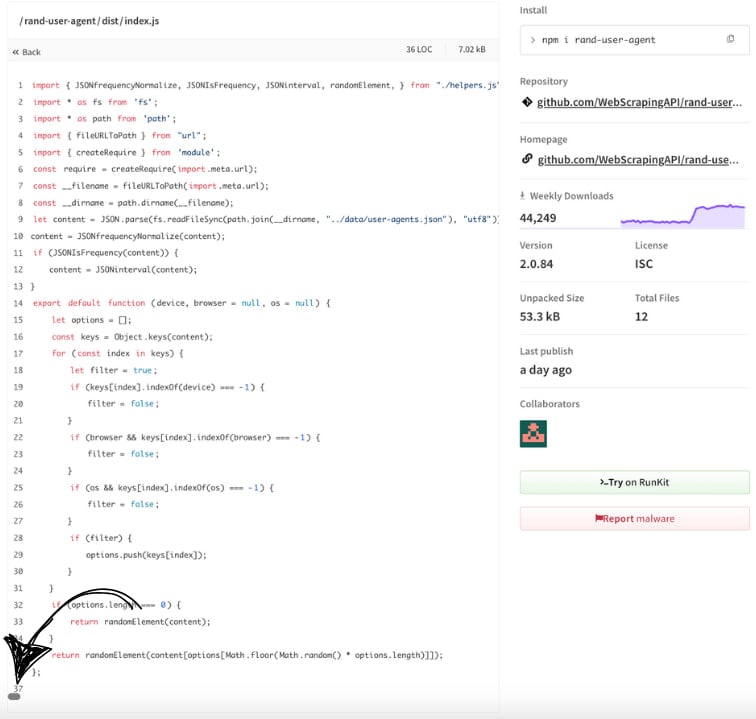
Source: Aikido
The investigation revealed that the final valid edition of the ‘Rand-User-Egent’ released 7 months ago was 2.0.82.
Version 2.0.83, 2.0.84, and 1.0.110, which were later published, were all malicious and not releasing the same on the Github repository of the project.
In the latest versions, embedded malicious code makes a hidden directory under the user’s home folder (~/.node_Modules) and expands the ‘module.
Subsequently, it opens a frequent socket connection for the command and control (C2) of the attacker at http: /85.239.62 (.) 36: 36: 36: 36: 36: 36: and sends machine ID information including Hostname, Useraname, OS, OS and a generated UUID.
Once the rat is active, it hears one of the orders given below:
- CD
– Changes in current working directory - Ss_dir – Reset the worker for the script path
- SS_FCD:
– Forced change in the given directory - SS_UPF: F, D – Uploads a single file F to Destination D
- SS_UPD: D, Dest – Directory uploads all files in D
- Ss_stop – Disrupts any ongoing file upload
- (any other) – Executes it as a shell command using Child_Process.exec ()
At the time of writing, malicious versions have been removed from the repository of the package on NPM, so the latest available version is safe, and users should return it.
However, if you have upgraded to version 2.0.83, 2.0.84, or 1.0.110, it is important to scan a full system for signs of compromise. Note that the rat is not removed from your system by downgrading in a valid version.
In addition, consider using the forkade but still supports the supported and better monitoring of the ‘Rand-Uzer-agent’ tool.
Bleepingcomputer approached the developer to find out how his package was compromised, and we got the following comments:
“5 May 2025 (16:00 UTC) was alerted to us that three unauthorized versions of the Rand-Uzer-agent were published in the NPM Registry (1.0.110, 2.0.83, 2.0.84). Maladient code was never present in our GITHUB Reposite;
Our investigation (still running) suggests that the opponent received an old automation token from an employee and used it to publish the release of NPM. The token was not scoped with a 2-factor authentication, allowing the attacker: to publish versions present in Github, to see the version numbers legitimately, nothing is expected to happen, expected that the new release will be promoted before seeing anyone.
There is no evidence of violation of our source-code repository, build pipeline, or corporate network. The incident was limited to the NPM registry.
We apologize to every developer and organization affected by this incident. Protecting the open-source ecosystem is a responsibility that we take seriously, and we are committed to complete transparency because we stop every difference that allowed this attack to happen. ,
Update 5/9 – Comment added from webscrapingapi \ _



