The UK National Cyber Security Center (NCSC) has formally blamed ‘Authentic Antics’ detective malware attacks for APT28 (fancy bear), a threat that is already associated with Russia’s military intelligence service (GRU).
The NCSC on 6 May revealed in a detailed technical analysis of authentic anteics malware that it is stealing credentials and OAuth 2.0 tokens that allow access to the target email account.
The malware was seen in 2023 and runs inside the outlook process and produces several microsoft login signals in its efforts to intercept the victim’s sign-in data and authority code.
The agency says that because Microsoft 365 apps are configured per tenant per tenant, it is possible that sensitive data also works for online exchange, sharepoint and ONEDRIVE.
The authentic anteics hide the operation by disabled to send the stolen data to an attacker-controlled email address using the victim’s own outlook account, and the “Save to be sent” option.
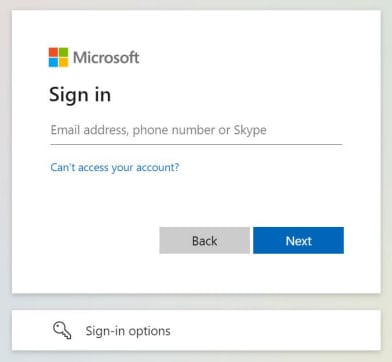
Source: NCSC
Authentic antics consist of many components including a dropper, a infoseller, and several powerrashel scripts.
The UK Cyber Agency says that authentic antics have a high level of sophistication that allows it to provide access to the suffering email accounts for a long time without detecting it.
This is possible because the network communication of malware is only with legitimate services. In addition, since it automatically sends the victim’s email messages to the attacker, he does not require command-end control (C2) server to achieve tasks.
“Its presence on the disc is limited, data outlook stored in specific registry locations,” NCSC experts have said in technical. Analysis,
Attention and restriction
The NCSC created any attention for authentic antics, but the agency today announced that it found evidence that the malware was linked to the APT28 State Group, which is also known as fancy bears, sednets, sofesi, pon stars, Storm, Strontium, TSAR team and Forest Blogs.
“The government today (July 18) has exposed Russian military intelligence actors to use unknown malicious software to enable espionage against the afflicted email accounts, in a move that will protect the UK and its colleagues,” NCSC says,
“The National Cyber Security Center – a part of the GCHQ – has revealed for the first time that Cyber Threat Group APT 28 is responsible for deploying a sophisticated malware dubged authentic antics as part of its operation.”
This attention has also done Government of UK approves three GRU units (26165, 29155, and 74455) and 18 Russian persons These and other related campaigns include.
UK officials condemned the GRU agents to volatile Europe and to endanize British citizens, also said that the deployment of authentic antics reflects the increasing refinement for Russian intelligence service.
At the same time, he outlined the NCSC’s commitment to highlight these cyber activities and approve responsible parties.
Authentic antics have been used in attacks
CISOS knows how to purchase a board begins with a clear, strategic approach how the cloud safety runs the business price.
This helps to introduce the risk, impact and priorities to the free, editable board report deck deck security leaders in clear business terms. Convert security updates into meaningful conversations and take fast decision in boardroom.



