
Windows 10 KB5058379 Cumulative Update is triggering the unexpected Bitalocker Recovery Prompt on some devices and has been installed and the computer has been resumed.
On 13 May, Microsoft issued a cumulative update as Windows 10 KB5058379 as part of its May 2025 patch Tuesday update. This is a mandatory update as it includes security updates for the weaknesses fixed by Microsoft, including five actively exploited zero-day flaws.
As first seen Windows LatestSince the release of this update, some Windows users and administrators are reporting that the computer will automatically boot into the Vinkar Bitalocker recovery screen, after installing the update and restoring the device.
Although it is not affecting all Windows devices, some devices have enough reports to indicate a problem with updates.
A Windows Admin posted, “We have about half a dozen laptops, which after receiving the same KB experienced various stolen issues – some require a Bitaloker’s keys to start some, refusing to start others,” a Windows Admin posted. reddit,
“The latest KB5058379 released on 13 May, the quality update failed in Windows 10 devices. Some devices triggers Bitaloker key window after restarting it,” another person posted. Microsoft forum,
Soon after, many people reacted to the post that the devices in their organizations were booting in vinere and then showed Bitlocker recovery screens.
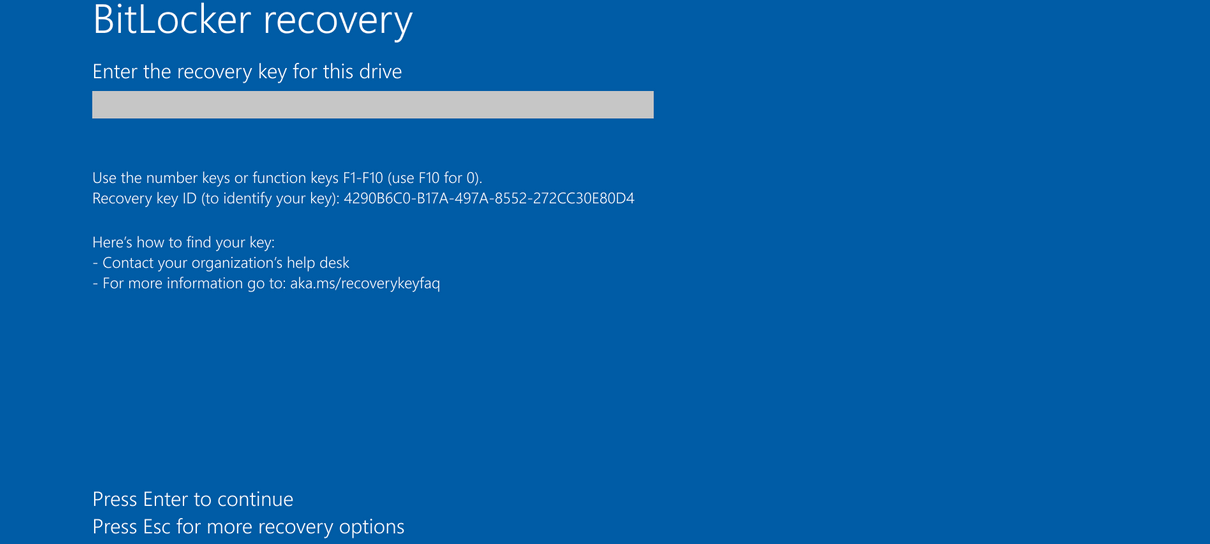
Source: Microsoft
The report of Lenovo, Dell and HP equipment is being affected by this issue, so it is not clear what special hardware or setting struggle is happening.
Some users reported on Reddit that they can re -boot into Windows by disabled in the BIOS by disabled by the Intel Trusted Execution Technology (TXT).
Trusted Execution Technology (TXT) is a hardware-based security facility that verify the integrity of system components before allowing sensitive operations to run.
While Microsoft has not publicly accepted the issue, Microsoft support reportedly told a user that they were aware of the issues.
“I would like to inform you that we are currently experiencing a known issue with the patch of the month of May. KB5058379In the title “Windows 10 tools after installing Bitalocker Recovery KB5058379” On Windows 10 machines, “an affected user posted reddit,
“A support ticket with the Microsoft Product Group (PG) team has already been raised, and they are actively working on a resolution.”
Microsoft then shared the following steps to users to return to Windows.
1. Disable safe boot
- Reach the BIOS/firmware settings of the system.
- Find out Safe boot Option and set it disabled,
- Save changes and reboot the device.
2. Disable virtualization technologies (if the problem persists)
- Repeat the BIOS/firmware settings.
- Disable all virtualization options, including:
- Intel VT-D (VTD)
- Intel VT-X (VTX)
Note: This action can indicate for Bitalocker recovery key, so please make sure that the key is available.
3. Check Microsoft defender system guard firmware security status
You can verify it in one of the two methods:
- Registry system
- Open Registry Editor.
- Navigate: hkey_local_machine \ System
- Check competent dword value:
- 1 → firmware is able to security
- 0 or missing → firmware security is disabled or not configured
- GUI method (if available)
- open Windows Security> Device SecurityAnd look down Core isolation Or Firmware protection,
4. Disable firmware protection through group policy (if banned by policy)
If firmware security settings are hidden due to group policy, follow these steps:
- Using group policy editor
- Open gpedit.msc.
- Navigate: Computer Configuration> Administrative Template> System> Device Guard> Turn on virtue based security
- Under Safe projection configurationSet option disabled,
- Or through registry editor
- ,
- “Saksham” = DWORD: 00000000
Important: To make this change effective, a system requires restart.
It is strongly encouraged to disable TXT in BIOS before disabled safe boot or virtualization features, as disabled can have a significant impact on the use of the device, performance and virtue of the device.
Bleepingcomputer did not test these workarounds, so first test them before fixing many devices.
Bleepingcomputer contacted Microsoft to learn more about the issue and will update the story if we get a response.



