More than 9,000 Asus routers were quietly hacked, and if you own one, there is a chance that you are in that list. Fortunately, you do not have to wait for things to go south to find out.
More than 9,000 Asus routers compromised in the ongoing attack
A cyber security firm, GranoisThere is a claim to identify an “ongoing exploitation campaign” affecting thousands of ASUS routers in touch with the Internet.
The report stated that the attackers behind the campaign, who are unknown, have achieved unauthorized and frequent access to more than 9,000 Asas routers. Depending on their strategy,, including stealth early access to control and misuse of underlying system facilities, Greenois says that the activity points to a well -revived and highly capable opponent, in line with people seen in advanced, long -term campaigns.
The attackers allegedly used Brut-Fores Login attempts and two different authentication methods. After successfully accessing Asus routers, he exploited a known vulnerability (Cve-2023-39780) To run arbitrary command. Through this, he enabled ssh access if it was not already active and put his public SSH key, providing frequent access.
Since the SSH key is stored in non-vaporous memory (NVram) instead of a file system, it avoids reboots and firmware updates. Hackers disable the logging, removing any mark of their reach and took it one step forward. Surprisingly, the report claims that the attackers do not install any type of malware, which eventually leads to the question – why the attack? Greynoise says in his report:
This appears to be part of a stealth operation to collect a distributed network of back door equipment – potentially laying groundwork for future botnets.
If you do not know, a botnet refers to a network of kidnapped computers or equipment, which are used far away by all the attackers, used to scams and attacks. Usually, the best course of action in such cases will be to update your router’s firmware. However, doing so will not help here as the attackers are stored in the NVRAM of the router.

Connected
Does resetting the hacked router make it secure again?
So, you have been hacked to the router. The best solution is to reset hardware, but does it secure again? What should you know here?
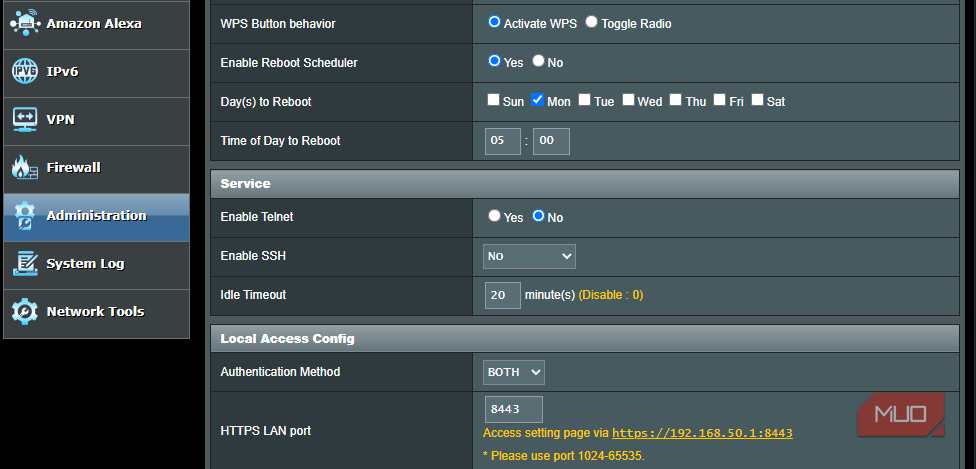
Thankfully, there is still a way to check if hackers managed to reach your asus router. You can do this by logging into the router firmware and heading Administration Section. Then look for Enable ssh option Below Service Header.
If your router has fallen victim to the attack, you will see that SSH Access is capable of an unusual port, especially Port 53282, as well as the following trunked SSH with public key: Ssh-Rsa aaaab3nzac1yc2eaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
Since a firmware update will not fix it, the best solution is to reset the factory to your router. Asus also recommends removing or disabled SSH entry along with blocking the following IP address: 101.99.91.151, 101.99.94.173, 79.141.163.179, and 111.90.146.237.
If you are one of lucky people, now there is a good time to update your router’s firmware, which is to prevent the future falling in the future. This is because Asus has fixed the CVE-2023-39780 blame that allowed hackers to run arbitrary commands on the router.