
Cyber security researchers discovered a vulnerability in McDonald’s, McDonald’s Chatbot Job Application Platform, which highlighted more than 64 million job applicants chat across the United States.
The defect was discovered by safety researchers Ian Carol and Sam Curry, who found that the administrator panel of the chatbot used a test franchise, which was preserved by a login name “123456” and a password of “123456”.
Mchire, operated by Paradox.ai and is used by about 90% of the McDonald’s franchise, accepts job applications through a chatbot called Olivia. Applicants can submit names, email addresses, phone numbers, home addresses and availability, and are required to complete a personality test as part of the job application process.
Once logged in, the researchers submitted a job application to the test franchise to see how the process works.
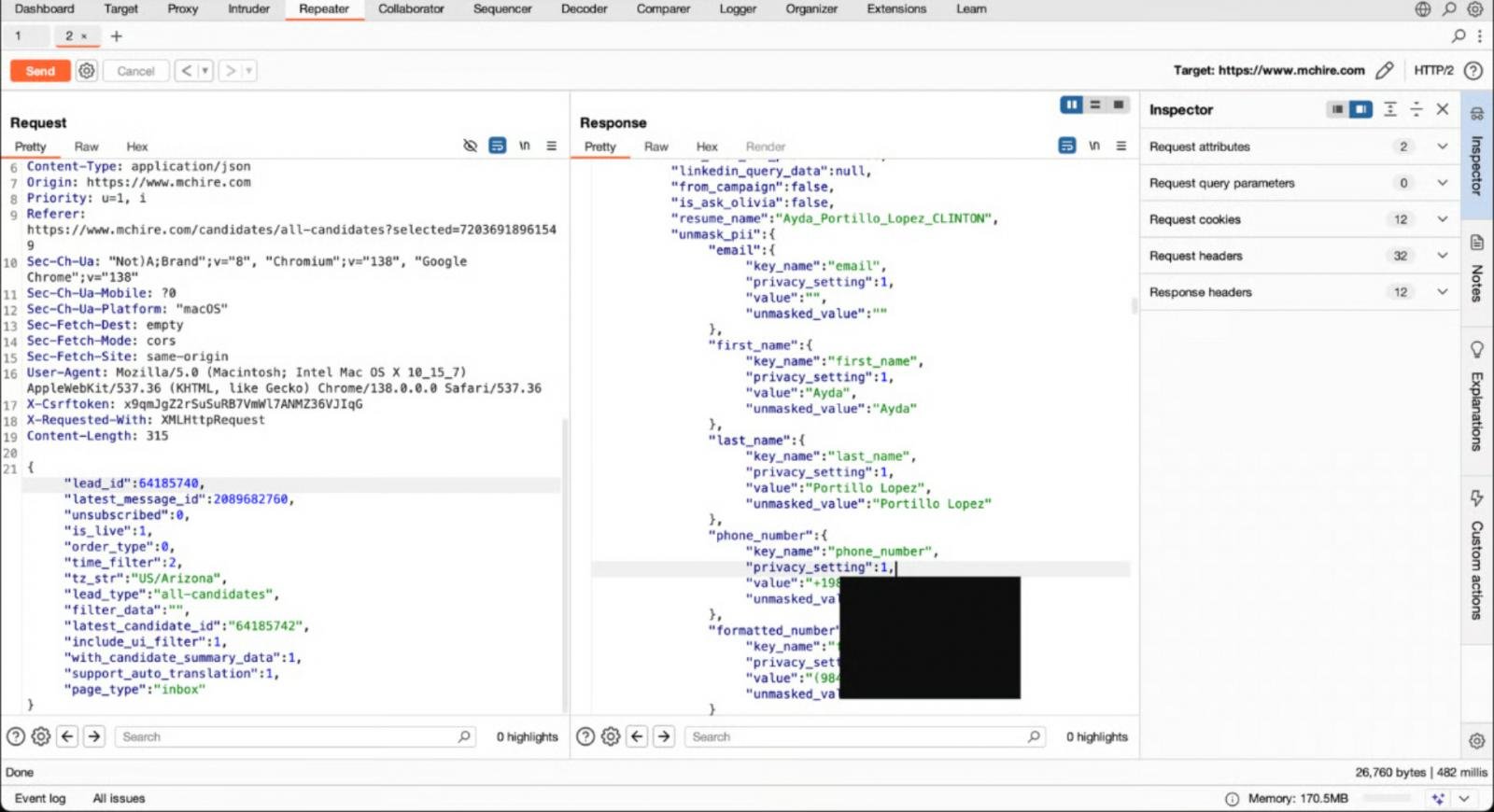
During this test, he noticed that the HTTP requests were sent to API & Point/API/Lead/CEM-Xhr, which used a parameter lead_ID, which was 64,185,742 in his case.
Researchers found that by increasing and decreasing the lead_ID parameters, they were able to highlight the personal data of full chat tape, session tokens and real job applicants who were first applicable to McHere.
This type of defect is called an IDOR (unprotected direct object reference) vulnerability, when an application exposes internal object identifiers, such as a record number, without verifying whether the user is really authorized to reach data.
“During a cursory security review of a few hours, we identified two serious issues: McHeire Administration Interface for the owners of the restaurant accepted the default credentials 123456: 123456, and an unsafe direct object reference (IDOR) on an internal API allowed us to use any contact and chat,” Carol. Explained in a rightup About the defect.
“Together they allowed us and someone else with a McHare account and access to any inboxes to regain personal data of more than 64 million applicants.”
In this case, in a request, the lead_ID number was raised or reduced or sensitive data related to other applicants was returned, as the API failed to check whether the user had access to data.
The issue was reported to Paradox.ai and McDonalds on 30 June.
McDonald’s accepted the report within an hour, and the default administrator Creedians were soon disabled.
McDonald’s said, “We are disappointed with this unacceptable vulnerability from a third-party provider, Paradox.ai. As soon as we learned about the issue, we made Paradox.ai mandatory to immediately remove the issue, and it was resolved on the same day that we were told,” McDonldes told. Wire In a statement about research.
Paradox deployed a fix to address the Ider Flaw and confirmed that vulnerability was reduced. Paradox.ai is Since it is said It is reviewing its system to prevent similar major issues from recurring.
Paradox also stated bleepingcomputer that information would be any chatbot interaction, such as clicking on a button, even if no personal information has been recorded.
Update 7/11/25: Information was added from the contradiction.



