
The doctors API, who targeted a danger actor, has updated his malicious tooling with a more dangerous functionality that can lay the foundation for a complex botnet.
The activity was first reported by Cyber Security Company Trend Micro in June. Whose researchers analyzed the script and malicious code, which dropped a cryptominer and trusted the Tor Network to hide their identity.
Akamai researchers discovered the new tooling that does not deploy a minein, but is a more complex payload that can block access to the compromised doors API.
Transition chain
The attackers discover the revealed on a weak host, search for API (Port 2375) and send a container manufacturing request using a modified Alpine Linux image consisting of a base 64-encoded shell command.
Container executes decoded shell command, which installs Karl And TORLaunches a tor Damon in the background, and arrives at Amazon and waits for the confirmation of the connection Checkip.amazonaws.com Serving a Socks5 Proxy.
Once the tor is active, the container downloads and uses a second-step shell script from a tor Hidden service. Karl,
docker-init.sh The script enables SSH access by connecting an attacker-controlled public key to/reot/. SSH/Authorized_Keys On mounted host filesistum.
It writes a base 64-Encoded Krone Job on the host, which executes every minute and also blocks external access to Port 2375 using Port 2375 using (IPTABles, NFTABles, UFW, etc.).
Additionally, it installs the device such as Maskan, Zstd, LibpcapAnd Torusox To support scanning, spread and theft.
Subsequently, the malware downloads a Zstandard-Compressed Go Binary (System-Linux-Cret. ZST), disintegrates it. /TMP/SystemThe grant executes permissions, and runs it.
The Go binary function as a dropper, to remove and execute an embedded second-step binary, and the log-in users pass the UTMP file of the host.
Source: Akamai
Botnet building behavior
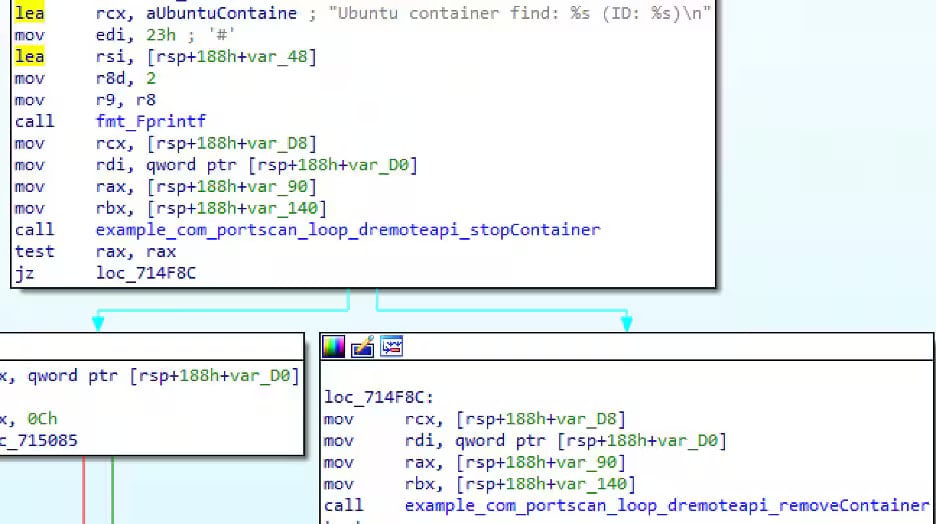
The binary scan for other exposed doors APIs, attempts to infect them through the same container manufacturing method, and removes competitive containers after achieving access.
This self-practice system is a main symptom of botnet agents that usually infects new nodes, without the need for the outer direction.
Source: Akamai
Akamai highlights the presence of passive argument to exploit the Tailnet (Port 23) to exploit the Tailnet (Port 23) to interact with the Chrome’s remote debugging interface (Port 9222).
This suggests opportunities for possible future expansion for credential theft, browser session kidnapping, remote file download, and distributed refusal-service (DDOS).
“Some underlying mechanisms inspire us to believe that this version is an early version of a complex botnet,” says researchers in Akamai. Focusable That they have not “found a complete version of it yet.”
The discovery of Akamai has shown development from an opportunistic doctor exploitation in a multi-sector threat to the lateral movement, firmness, and (passive for now), which is an option to credential theft and browser kidnapping.



