
Salesforce confirmed that it will not interact with the actors who threatened or give them ransom this year with a large wave of data theft attacks affecting the company’s customers.
As reported for the first time BloombergSalesforce on Tuesday emailed the customers that they would not give ransom and warned that “reliable danger intelligence information” indicated that the danger actors were planning to leak the stolen data.
Salesforce also confirmed from the blemping computer, “I can confirm that salesforce will not involve, interact or pay.”
The statement came after the launch of the data leak site by dangerous actors known as “Scattered Lapsus $ Hunters”, trying to extort forcibly from 39 companies whose data was stolen from salesfors. The website Brechforams (.) The HN Domain was located on the domain, named after the notorious Breechforams website, a hacking forum known for selling and leaking the stolen data.
Fedex, Disney/Hulu, Home Depot, Marriott, Google, Cisco, Toyota, Gap, Carring, McDonald’s, Walgings, Instacc, Cartier, Adidas, Sek Fifth Avenue, Air France and KLM, HBO Max, HBO Max, HBO Max, HBO Max, Chill Famous brands and organizations including IKEA were included.
Overall, the threatened people claim to steal about 1 billion data records, which will be publicly released if forcible recovery is sought by individual companies or all affected customers listed on the site as single payment from salesfors will be covered.
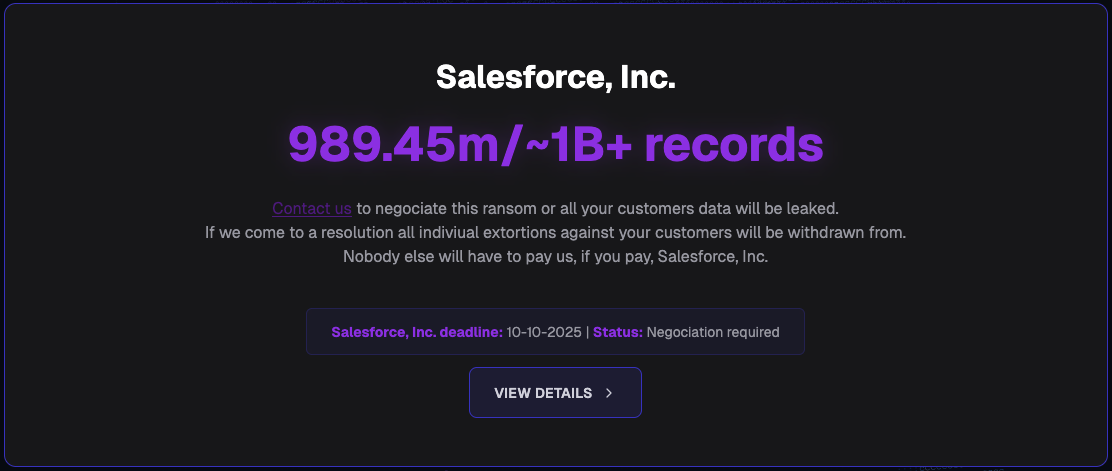
Source: Bulping Computer
This data was stolen from salesforce instance in two separate campaigns in 2025.
The first data theft campaign began at the end of 2024, when threatening actors began carrying out social engineering attacks by taking the form of an IT support staff to cheat the employees with their company’s salesforce institute.
Once the link was linked, the threatening actors used connections to download and steal the database, which was used to forcibly recover the company via email.
These social engineering attacks affected GoogleCisco, Quantas, Adidas, Allianz Life, Kisan Insurance, Workday, Carring, and LVMH subsidiaries, such as Dyer, Louis Wuiton, and Tiffany & Co,
The second salesforce data-chori campaign began in early August 2025, when threatening actors used the stolen salesloft drift OAThe tokens to create axis in the CRM environment of customers and remove the data.
Salesloft data-chori attacks were mainly focused on stealing support ticket data to scan credentials, API tokens, authentication tokens and other sensitive information that enabled the attackers to make a dent in the company’s infrastructure and cloud services.
One of the dangerous actors behind the Celseloft attacks, known as Shineans, told the Bleeping Computer that he stole nearly 1.5 billion data records of more than 760 companies during the campaign.
Many companies have already confirmed that they have been influenced by the salesloft supply-chain attack, including Google, Cloudflare, Zscler,. Worthy, Cyberark, Elastic, Beyond faith, Authentic, Zeffron, Nutanix, Qualis, Rubric, Cutto networkPalo Alto Network, and Too much,
The recently launched data leak site was used mainly to make forcibly recovery from customers in the original social engineering attacks, stating that they would start publicly recovering from people affected by the salesloft attacks after 10 October.
Although the data leak site is now closed, the domain is now using the nemsarwar of surina.ns.cloudflare.com and haans.ns.cloudflare.com, which has both Was used by FBI in the past While seizing the domain.
Bleeping computer contacted the FBI about whether he had seized the domain but did not get any response at this time.



