
Scattered Spider Hackers have aggressively targeted the virtuous environment by attacking VMWARE ESXI hypervizer in American companies in retail, airline, transportation and insurance sectors.
According to the Google Threat Intelligence Group (GITG), the attackers continue to employ their general strategy, which do not include vulnerable exploits, but rely on fully executed social engineering “to bypass mature security programs.”
A scattered spider attack
Researchers say that the gang starts an attack by applying an employee in the call to the IT help desk. The actor’s purpose is to change the agent to change the employee’s active directory password and thus achieve the initial access.
This allows scattered spider to scan network devices for IT documentation that will provide high-value targets, such as domains or VMware VSPHERE Names of Administrators, and Safety Group that can provide administrative permissions on the virtual environment.
At the same time, they scan for privileged access management (PAM) solutions that can keep sensitive data useful to go into valuable network assets.
“Armed with a specific, high -value administrator’s name, they make additional calls on the help desk. This time, they replicate the privileged user and request a password reset, allowing them to seize a privileged account control” – Google Danger Intelligence Group
Hackers then do their jobs to get access to the company’s VMware VCenter Server Equipment (VCSA) – a virtual machine that allows the VMWARE VSPHERE environment to manage the environment, which includes ESXI hypergear for managing all virtual machines on a physical server.
This level of access allows them to enable SSH connections on the ESXI host and reset the root password. In addition, they execute a so-called “disc-swap” attack to extract significant ntds.dit databases for the active directory.
A disk-SWAP attack occurs when the actor closes a domain controller virtual machine (VM) and controls precious VMs, to attach his virtual disc only to another. After copying sensitive data (eg ntds.dit file), they return the process and power on the domain controller machine.
It is important to note that the level of scattered spider scattered on virtual infrastructure allows them to manage each property available, including backup machines, which eradicate backup jobs, snaphots and repository.
Spider scattered in the final stages of the attack availed its SSH access to distribute and deploy rangesware bioneries to encrypted all the VM files discovered in the datastor.
Based on their comments, GTIG researchers say that a scattered spider attacks have five different stages that allow hackers to move from low-level access to take full control over hypervizers.
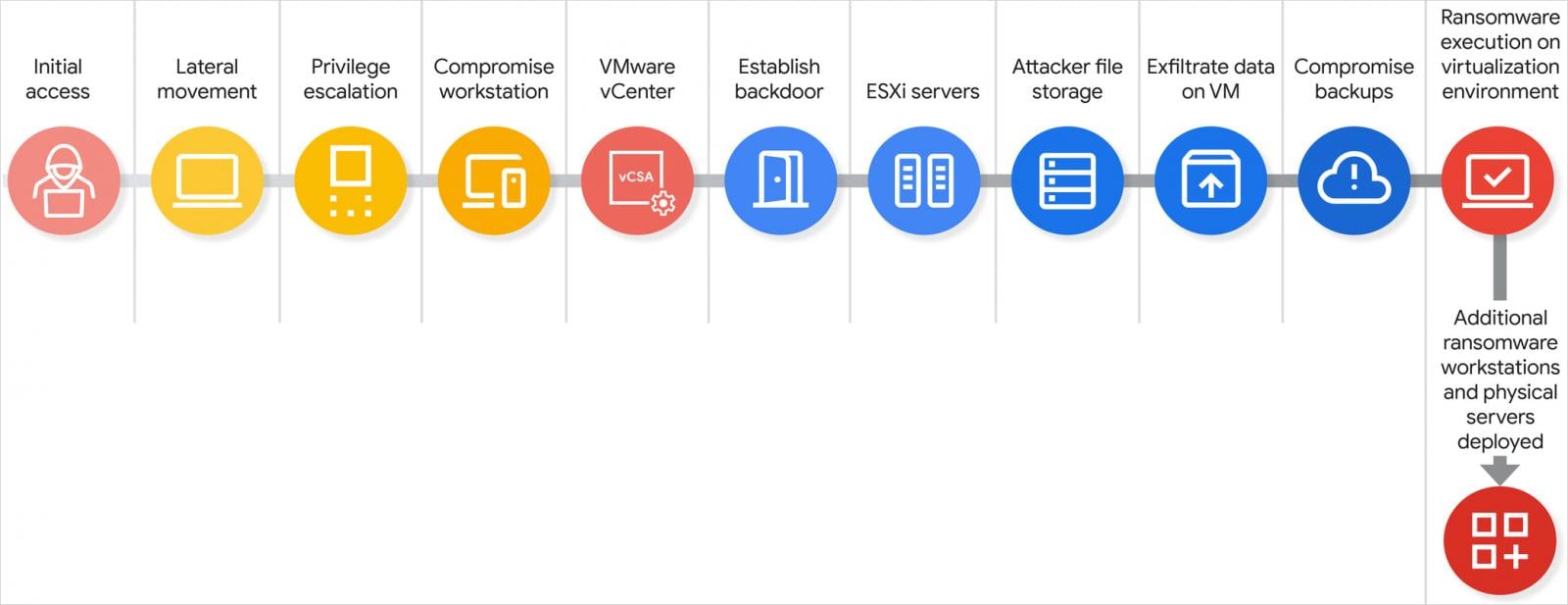
Source: Google
A scattered spider attack chain, which can be completed by early access to data exfIs and ransomware sins, can occur in a few hours.
A representative of Google told Bleepingcomputer that without exploiting any software weaknesses, the actor “manages to achieve an unprecedented level of control over a complete virtual environment.
While the target of ESXI Hyperviser is not new (Spider scattered in the 2023 MGM resorts attacks has been seen in high-profile violations) GTIG notes states that they are looking at more rangesy groups and expecting the problem.
One of the reasons behind this may be that opponents have seen that VMware infrastructure is often poorly understood by organizations and as a result, not so strongly protected.
To help organizations protect from these attacks, google Published a technical post Describing the stages of a scattered spider attack, describing why it is efficient, and providing action that a company can take to detect violations in the earlier stage.
The proposed measures can be summarized in three main columns:
- Lock the vsphere with Execinstalledonly, VM encryption and disabled ssh. Avoid joining direct advertisements on ESXI, remove orphan VM, and apply strict MFA and access policies. Constant monitor for configure flow.
- Use fishing-resistant MFA in VPN, AD and VCenter. Separate the tier 0 assets (DCS, backup, PAM) and avoid hosting them on the same infrastructure that they secure. Consider separate cloud IDP to break advertising dependence.
- Centrally centralize the log in a siem and warn on major behaviors, such as the administrator group change, VCenter login and SSH enabled. Use irreplaceable, air-gapsp backup and test recovery against hyperchiers-layer attacks.
Scattered Spider (also known as UnC3944, Octo Tempest, 0ktapus) is an economically motivated danger group, especially at a level in social engineering, which can apply the employees of the company using proper vocabulary and pronunciation.
It has recently raised its activity with attacks on large UK retail firms, airlines and transportation institutions and insurance companies.
Although the UK’s National Crime Agency arrested four suspected members of the group, the malicious activity arising from other groups has not decreased.
CISOS knows how to purchase a board begins with a clear, strategic approach how the cloud safety runs the business price.
This helps to introduce the risk, impact and priorities to the free, editable board report deck deck security leaders in clear business terms. Convert security updates into meaningful conversations and take fast decision in boardroom.



